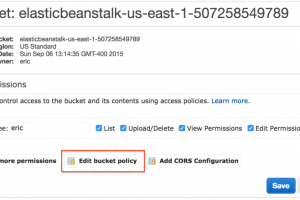
Discovered by UpGuard defense researcher Chris Vickery, the databases were entitled “CENTCOM-backup,” “CENTCOM-archive,” and “pacom-archive.” Based on their...
Author - Mazen Elzanaty
SpookFlare has a different perspective to bypass security measures and it gives you the opportunity to bypass the endpoint countermeasures at the client-side...
The firm looked at nearly 70 million emails sent during October from 5,000 different .gov origin domains preserved by Proofpoint, the company’s VP of Email...
Security researchers have discovered a new, sophisticated form of malware based on the notorious Zeus banking Trojan that steals more than just bank account...
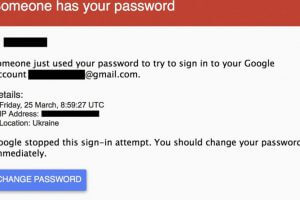
Now security researchers have discovered that the camera can be silenced and frozen from a script run from any machine within Wi-Fi range, reports News. That...
Prochunter aims to find hidden process with all userspace and most of the kernelspace rootkits. This tool is composed of a kernel module that prints out all...
Features Auto VoIP/UC penetration test Report generation Performance RFC compliant SIP TLS and IPv6 support SIP over websockets (and WSS) support (RFC 7118)...
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
Enigma is a Multiplatform payload dropper. Run git clone cd Enigma python enigma.py or python3 enigma3.py Prerequisites python 2.7 for enigma.py python 3.x for...
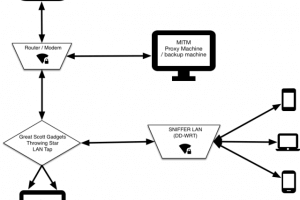
Essentially it’s a WiFi hotspot that is continually collecting all the packets transmitted across it. All connected clients’ HTTPS communications are subjected...