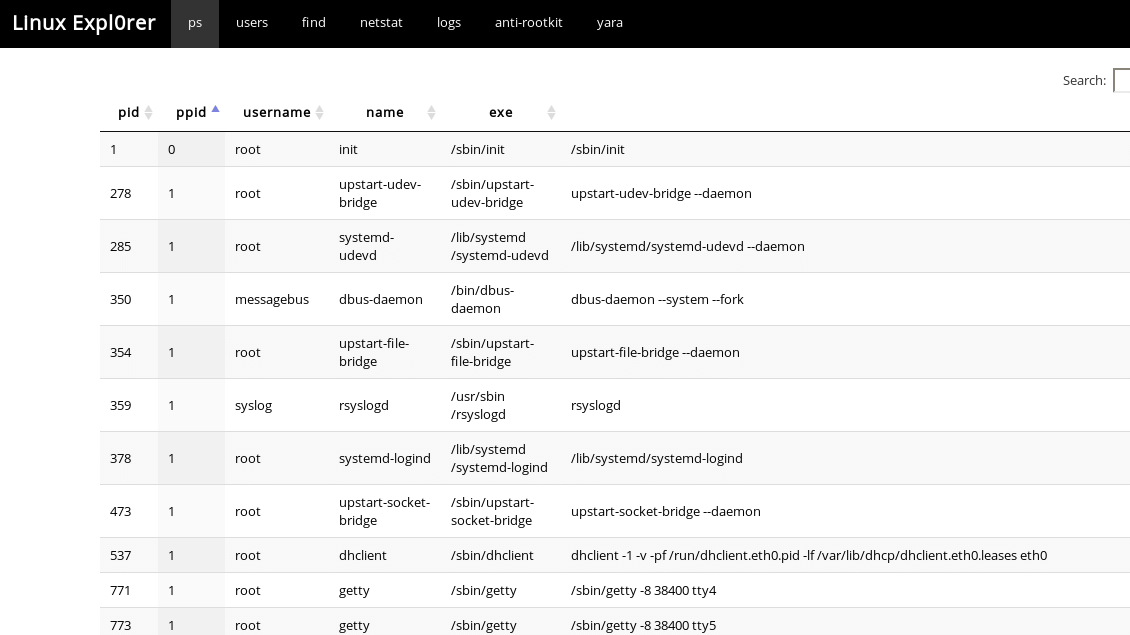
Easy-to-use live forensics toolbox for Linux endpoints written in Python & Flask. Capabilities ps View full process list Inspect process memory map &...
Author - Mazen Elzanaty
On December 14, the company will vote to repeal the net neutrality practices it put in place in 2015. With Republicans agents who oppose the rules outnumbering...
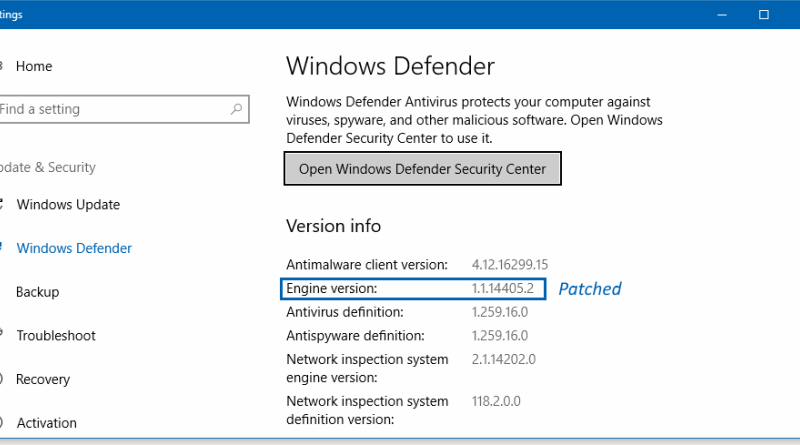
On Wednesday, Microsoft has released a patch for the Microsoft Malware Protection Engine (MPE) to fix a critical severity remote code execution (RCE) flaw in...
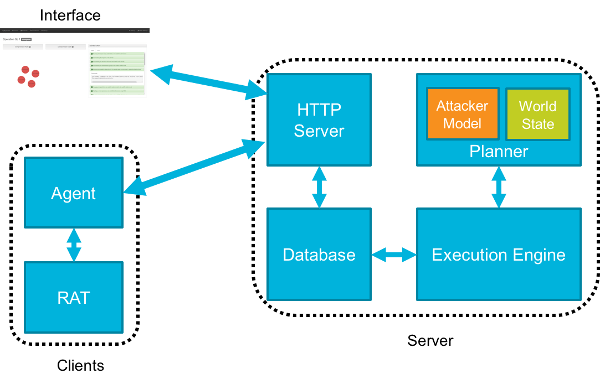
CALDERA is an automated adversary emulation system that performs post-compromise adversarial behavior within enterprise networks. It generates plans during...
Aletheia is a steganalysis tool for the detection of hidden messages in images. The goal of steganalysis is to identify suspected packages, determine whether...
Apple is one of the biggest companies today, but its devices are not free from issues. Recently, it was reported that the company’s HomeKit software used to...
Denis Sinegubko (a security researcher from Sucuri) has discovered a new wave of the known malware wp-vcd that injects malicious WordPress admin users into...
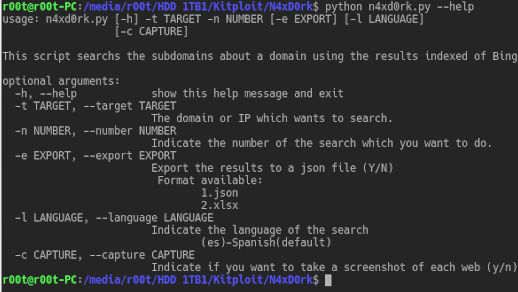
Listing subdomains about the main domain using the technique called Hacking with search engines. Usage usage: n4xd0rk.py [-h] [-d DOMAIN] [-i IP] -o OPTION -n...
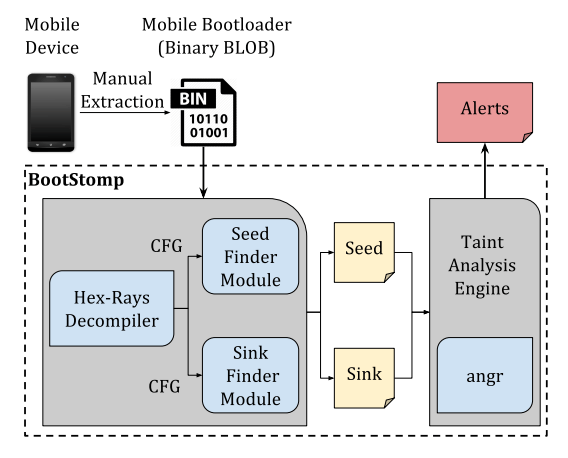
BootStomp is a boot-loader bug finder. It looks for two different class of bugs: memory corruption and state storage vulnerabilities. For more info please...
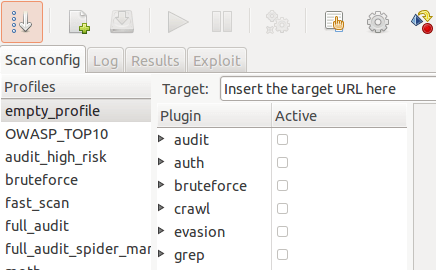
w3af is an open source web application security scanner which helps developers and penetration testers identify and exploit vulnerabilities in their web...