Recently, Triconex Industries was put at risk when hackers attempted to hack into its security systems, trying to control things. These attacks have a pattern...
Author - Mazen Elzanaty
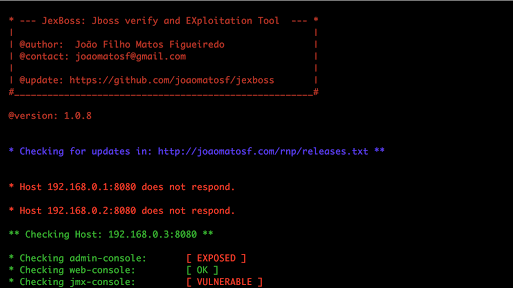
JexBoss is a tool for testing and exploiting vulnerabilities in JBoss Application Server and others Java Platforms, Frameworks, Applications, etc. Requirements...
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
Last week, security researchers have published the details of two possibly critical flaws affecting version 5 of the vBulletin forum software. vBulletin is the...
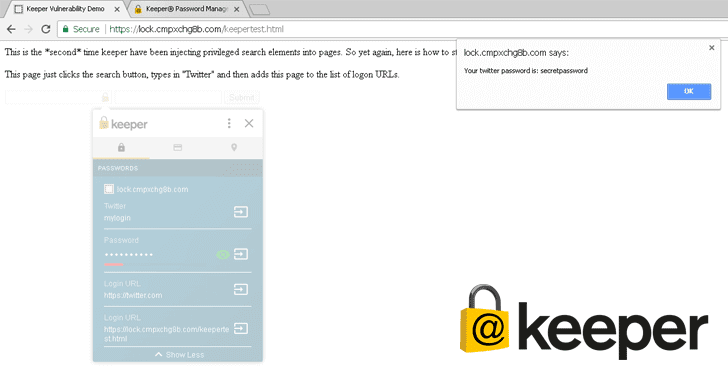
If you are running Windows 10 on your PC, then there are chances that your computer contains a pre-installed 3rd-party password manager app that lets attackers...
ADRecon is a tool which extracts various artifacts (as highlighted below) out of an AD environment in a specially formatted Microsoft Excel report that...
“This is the start of a long legal battle. Netflix stands w/ innovators, large & small, to oppose this confused FCC order,” the company tweeted quickly...
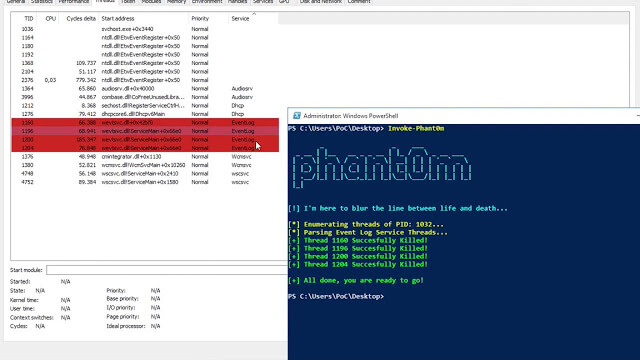
This script walks thread stacks of Event Log Service process (spesific svchost.exe) and identify Event Log Threads to kill Event Log Service Threads. So the...
Wifiphisher is a security tool that mounts automated victim-customized phishing attacks against WiFi clients in order to obtain credentials or infect the...
As per many security reports, managements systems of buildings all over the world have improved dramatically, however, their security is still at a large risk...