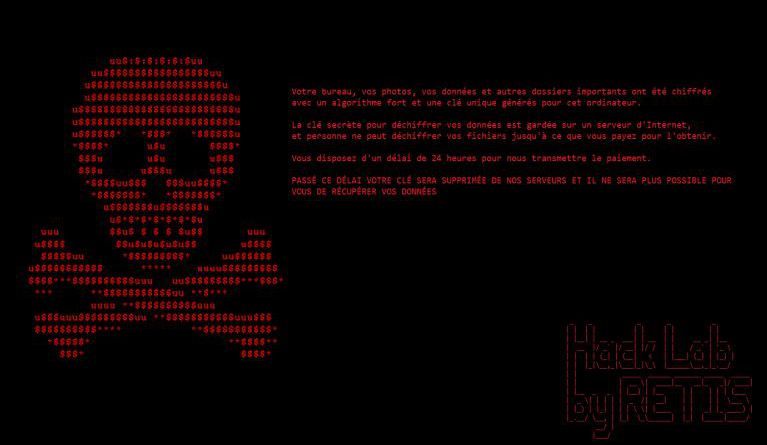
A security researcher has discovered a ransomware called Retis, which is a ransomware-type virus that secretly infiltrates the system. Shortly after executed, RETIS encrypts most saved data and adds filenames with the “.crypted” extension.
It is a .NET ransomware, so its source code can be easily viewed. When the malware executed it will first target the victim’s Desktop, Documents, and Pictures folder for encryption. After that, it will target the rest of the drives on the computer. Lastly, it will turn the Windows wallpaper as %APPDATA%\RANSOM.png, which is an installed resource in the executable. The executable also contains a second image resource of a mountain range, but it is not used.
The file extensions targeted by this ransomware are:
.txt, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .jpg, .jpeg, .png, .one, .pdf
The name of the ransomware is obtained from the string of text located in the windows console, it shows the string “Hack Lab by Retis”.
Retis ransomware shares several likenesses with dozens of other ransomware viruses such as Cyclone, Zlocker, and Skeleton.
Most ransomware is increased using spam emails, third-party software download sources, fake software updates, and trojans. Users are recommended to be careful, don’t open files (malicious attachments) received from suspicious email addresses – remove these emails without reading.





















Add Comment