State-of-the-art password guessing tools, such as HashCat and John the Ripper (JTR), enable users to check billions of passwords per second against password...
Archive - January 2018
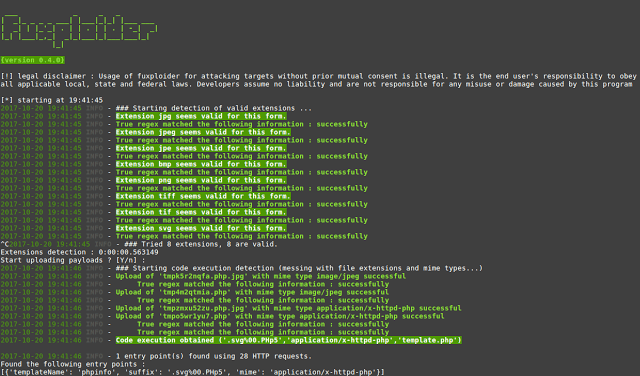
fuxploider is an open source penetration testing tool that automates the process of detecting and exploiting file upload forms flaws. This tool is able to...
ApkTool is a tool for reverse engineering 3rd party, closed, binary Android apps. It can decode resources to nearly original form and rebuild them after making...
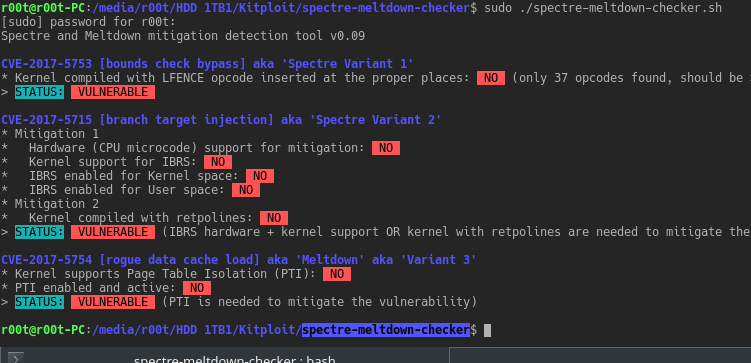
A simple shell script to tell if your Linux installation is vulnerable against the 3 “speculative execution” CVEs: CVE-2017-5753 bounds check...
Speculative optimizations execute code in a non-secure manner leaving data traces in microarchitecture such as cache. Refer to the paper by Lipp et. al 2017...
It’s time to learn how to renew its OS because researcher James Bercegay has found a dozen models possess a hard-coded backdoor. The backdoor, lets anyone log...
As the FCC has attempted to abandon its role as the defender of a free and open Internet at the federal level, states are attempting ways to step into the void...
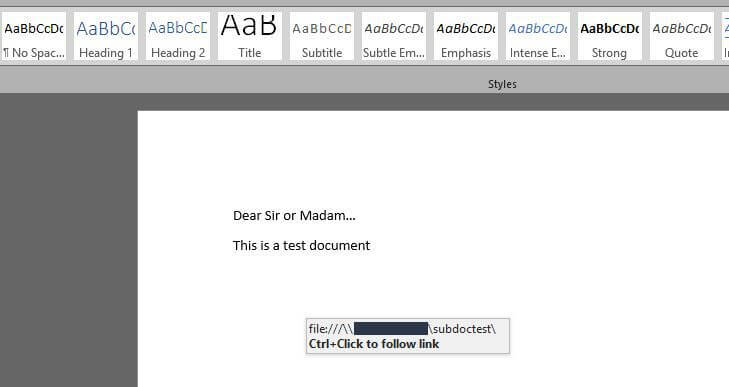
Security researchers from Rhino Labs (a US-based cyber-security firm) have found that cyber criminals can use a Microsoft Word feature dubbed subDoc to fool...
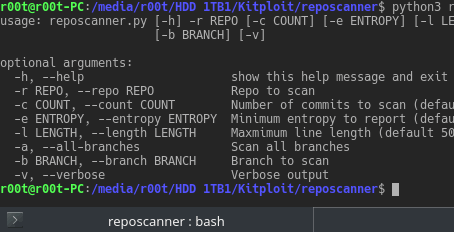
Reposcanner is a python script to search through the commit history of Git repositories looking for interesting strings such as API keys, inspires...
shimit is a python tool that implements the Golden SAML attack. python .\shimit.py -h usage: shimit.py [-h] -pk KEY [-c CERT] [-sp SP] -idp IDP -u USER [-reg...