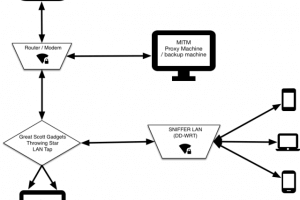
Essentially it’s a WiFi hotspot that is continually collecting all the packets transmitted across it. All connected clients’ HTTPS communications are subjected...
Archive - November 2017
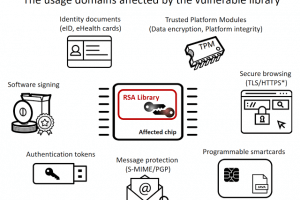
This tool is related to ACM CCS 2017 conference paper #124 Return of the Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli. It enables...
Another crop of Android apps hiding malware have been discovered in – and removed from – the Google Play store. Researchers at ESET discovered...
A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of...
This hack was not conducted in a laboratory, but on a 757 gathered at the airport in Atlantic City, N.J. And the real hack happened over a year ago. We are...
Right now, while artificial intelligence is concentrating on profit-generation, natural knowledge has proven to be higher than up to the task of manipulating...
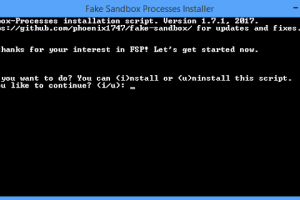
This small script will simulate fake processes of analysis, sandbox and/or VM software that some malware will try to avoid. You can download the original...
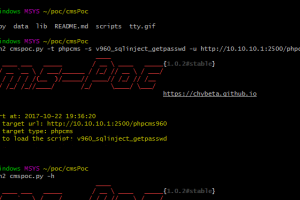
A CMS Exploit Framework. Requirements python2.7 Works on Linux, Windows Usage usage: cmspoc.py [-h] -t TYPE -s SCRIPT -u URL optional arguments: -h, --help...
Adobe’s latest security update has swatted a total of 67 bugs, some of them critical, in Adobe Flash, Acrobat, and Reader. On Tuesday, the software...
Forever 21 is investigating a potential data breach which may have compromised customer information and payment cards. On Tuesday, the US clothing retailer...