The official blog of jQuery—most popular JavaScript library used by millions of websites—has been hacked by some unknown hackers, using the pseudonym...
Archive - October 2017
Wesley Neelen (security researcher) has received a phishing email that seems to be from the legal online Ethereum wallet site Myetherwallet.com. Cybercriminals...
An unknown hacker has hijacked Coinhive’s DNS server and modified the legitimate Coinhive JavaScript in-browser miner with a malicious one that mined Monero...
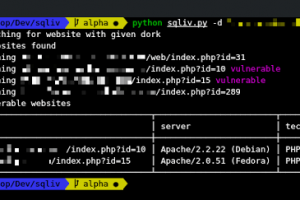
Massive SQL injection vulnerability scanner. Features multiple domain scanning with SQL injection dork by Bing, Google, or Yahoo targetted scanning by...
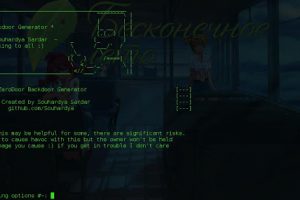
A script written lazily for generating reverse shell backdoors on the go whenever you need without any hassle for your daily penetration needs . These...
Reptile is a LKM rootkit for evil purposes. If you are searching stuff only for study purposes, see the demonstration codes. Features Give root to unprivileged...
According to various cybersecurity firms, the growing virus is dubbed “BadRabbit” and is a form of ransomware that bolts down machines and requires bitcoin...
News reported the issue, revealing a picture of a Pixel 2 XL with some fierce image remembrance around the navigation bar. Shortly after, numerous other...
81 percent of data breaks last year involved weak, default or stolen passwords, and phishing attacks have advanced 65 percent year-on-year. Protecting online...
DUHK (Don’t Use Hard-coded Keys) is a new crypto implementation attack that could enable attackers to obtain secret keys that secure VPN (Virtual Private...