TROMMEL sifts through directories of files to identify indicators that may contain vulnerabilities.
TROMMEL identifies the following indicators related to:
- Secure Shell (SSH) key files
- Secure Socket Layer (SSL) key files
- Internet Protocol (IP) addresses
- Uniform Resource Locator (URL)
- email addresses
- shell scripts
- web server binaries
- configuration files
- database files
- specific binaries files (i.e. Dropbear, BusyBox, etc.)
- shared object library files
- web application scripting variables, and
- Android application package (APK) file permissions.
TROMMEL has also integrated vFeed which allows for further in-depth vulnerability analysis of identified indicators.
Dependencies
- Python-Magic
- vFeed Database – For non-commercial use, register and download the Community Edition database
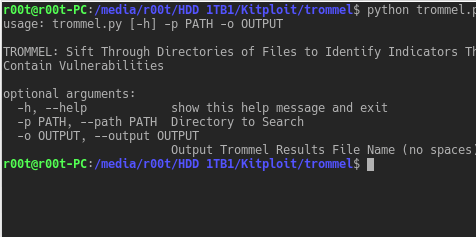
Usage
$ trommel.py --helpOutput TROMMEL results to a file based on a given directory
$ trommel.py -p /directory -o output_fileNotes
- TROMMEL has been tested using Python 2.7 on macOS Sierra and Kali Linux x86_64.
- TROMMEL was written with the intent to help with identifying indicators that may contain vulnerabilities found in firmware of embedded devices.
References
- vFeed
- Firmwalker
- Lua Code: Security Overview and Practical Approaches to Static Analysis by Andrei Costin



















Add Comment