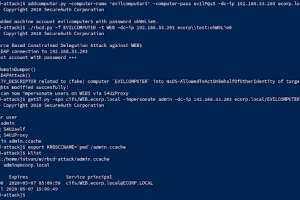
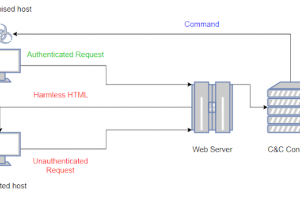
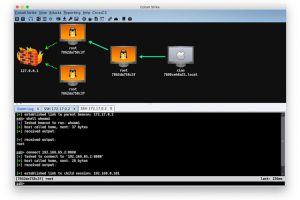
[sc name=”ad_1″] Abusing Kerberos Resource-Based Constrained Delegation TL;DR This repo is about a practical attack against Kerberos Resource-Based...
Tag - windows
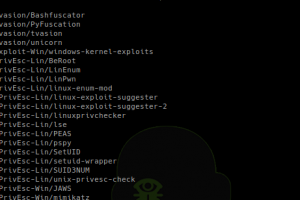
[sc name=”ad_1″] Some-Tools Why I was looking for a way to manage and keep up to date some tools that are not include in Kali-Linux. For exemple, I...
[sc name=”ad_1″] …a simple, self-contained modular host-based IOC scanner Spyre is a simple host-based IOC scanner built around the YARA...
[sc name=”ad_1″] Pentest Cyber Range for a small Active Directory Domain. Automated templates for building your own Pentest/Red Team/Cyber Range in...
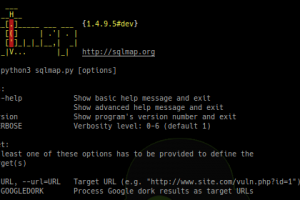
[sc name=”ad_1″] SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and...
[sc name=”ad_1″] There are better ways than managing vulnerabilities with spreadsheets, especially when you are working with several tools. We know...
[sc name=”ad_1″] SNIcat is a proof of concept tool that performs data exfiltration, utilizing a covert channel method via. Server Name Indication...
[sc name=”ad_1″] LOLBITS is a C2 framework that uses Microsoft’s Background Intelligent Transfer Service (BITS) to establish the...
[sc name=”ad_1″] A security framework for enterprises and Red Team personnel, supports CobaltStrike’s penetration testing of other...
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...