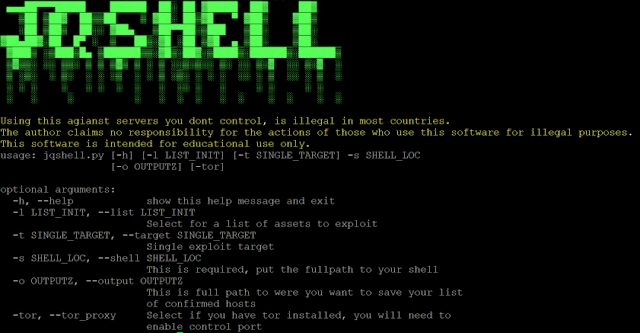
JQShell A weaponized version of CVE-2018-9206 (Unauthenticated arbitrary file upload vulnerability in Blueimp jQuery-File-Upload <= v9.22.0). Disclaimer...
Tag - tor
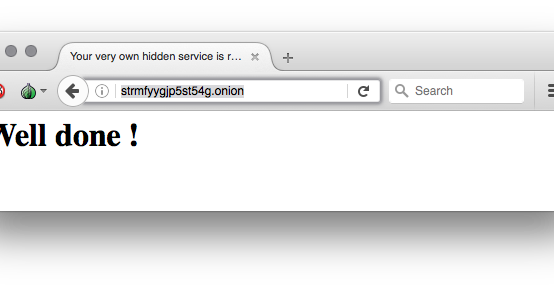
Easily run a hidden service inside the Tor network with this container Generate the skeleton configuration for you hidden service, replace for your hidden...
Tor enables users to surf the Internet, chat and send instant messages anonymously, and is used by a wide variety of people for both Licit and Illicit purposes...
Tool to check if a given IP is a node tor or an open proxy. Why? Sometimes all your throttles are not enough to stop brute force attacks or any kind of massive...
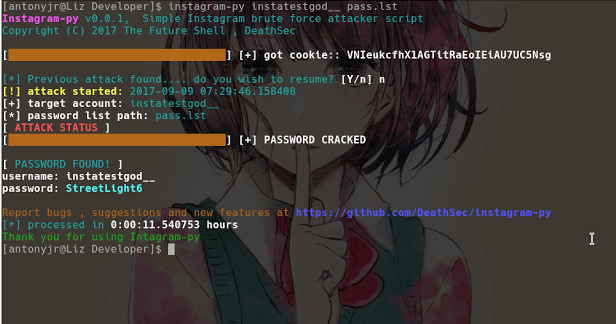
Instagram-Py is a simple python script to perform basic brute force attack against Instagram , this script can bypass login limiting on wrong passwords , so...
Take back your privacy. Lose yourself in the haystack. Your ISP is most likely tracking your browsing habits and selling them to marketing agencies (albeit...
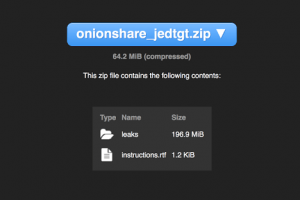
OnionShare lets you securely and anonymously share files of any size. It works by starting a web server, making it accessible as a Tor onion service, and...
Use nmap to scan hidden “onion” services on the Tor network. Minimal image based on alpine, using proxychains to wrap nmap. Tor and dnsmasq are run as daemons...
Exitmap is a fast and modular Python-based scanner for Tor exit relays. Exitmap modules implement tasks that are run over (a subset of) all exit relays. If you...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...