[sc name=”ad_1″] A bento (弁当, bentō) is a single-portion take-out or home-packed meal of Japanese origin. Bento Toolkit is a simple and minimal...
Tag - Security vulnerability
[sc name=”ad_1″] Process Herpaderping is a method of obscuring the intentions of a process by modifying the content on disk after the image has...
[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
[sc name=”ad_1″] What is cross-site scripting (XSS)? Cross-site scripting (also known as XSS) is a web security vulnerability that allows an...
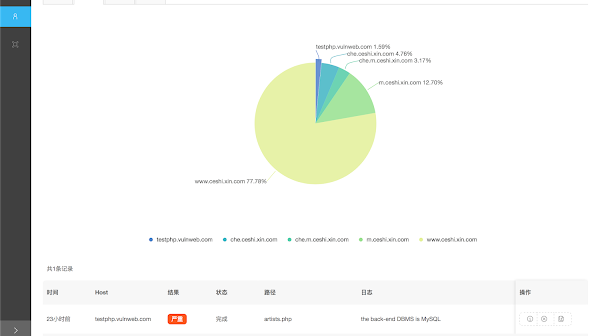
[sc name=”ad_1″] Automatic SQL injection with Charles and sqlmapapi Dependencies Django PostgreSQL Celery sqlmap redis Supported platforms Linux...
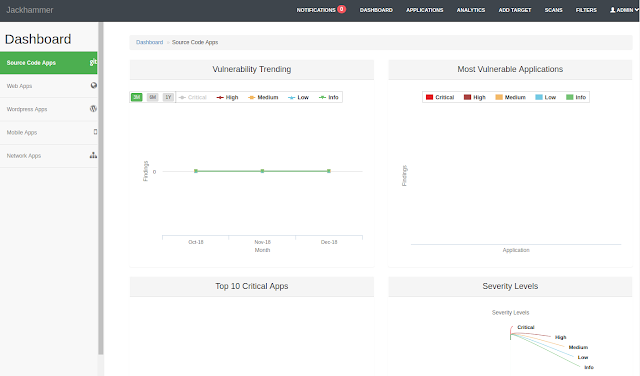
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...
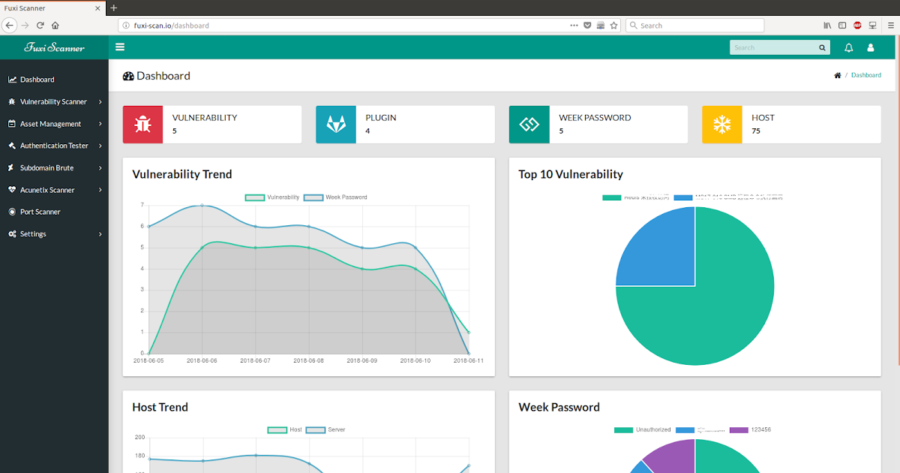
Fuxi Scanner is an open source network security vulnerability scanner, it comes with multiple functions. Vulnerability detection & management...
The flaw has been discovered by security researchers from the University of Birmingham, who tested hundreds of various banking applications and discovered that...