DET (is provided AS IS), is a proof of concept to perform Data Exfiltration using either single or multiple channel(s) at the same time. This is a Proof of...
Tag - Networking
The project is designed as a file resource cloner. Metadata, including digital signature, is extracted from one file and injected into another. Note: The...
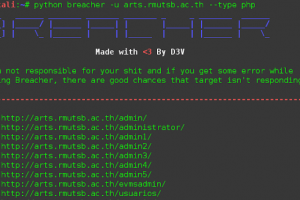
A script to find admin login pages and EAR vulnerabilites. Features Multi-threading on demand Big path list (798 paths) Supports php, asp and html extensions...
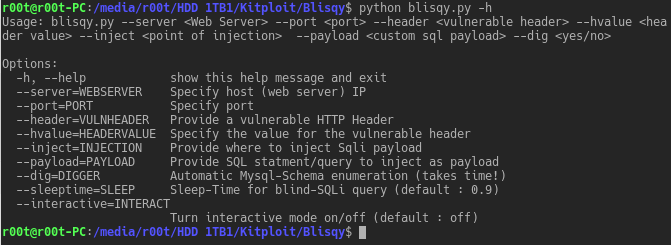
A slow data siphon for MySQL/MariaDB using bitwise operation on printable ASCII characters, via a blind-SQL injection. Usage USAGE: blisqy.py --server <Web...
It was used in an academic journal paper titled “Novel SIP-based DDoS Attacks and Effective Defense Strategies” published in Computers & Security 63 (2016)...
CuckooDroid is an extension of Cuckoo Sandbox the Open Source software for automating analysis of suspicious files. CuckooDroid brigs to cuckoo the...
Run PowerShell with dlls only. Does not require access to powershell.exe as it uses powershell automation dlls. dll mode: Usage: rundll32 PowerShdll,main...
Tails is a live system that aims to preserve your privacy and anonymity. It helps you to use the Internet anonymously and circumvent censorship almost anywhere...
pythem is a multi-purpose pentest framework written in Python. It has been developed to be used by security researchers and security professionals. The tool...
A python program to create a fake AP and sniff data new in 2.0: SSLstrip2 for HSTS bypass Image capture with Driftnet TShark for command line .pcap capture...