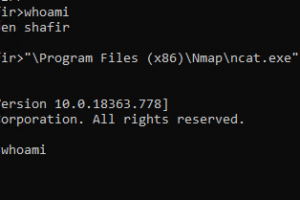
[sc name=”ad_1″] A Proof-of-Concept bind shell using the Fax service and a DLL hijack based on Ualapi.dll. See our writeup at: How to use Build...
Tag - Hijack
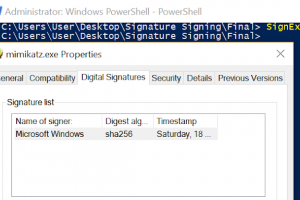
[sc name=”ad_1″] Hijacking legitimate digital signatures is a technique that can be used during red team assessments in order to sign PowerShell...
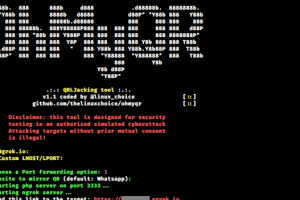
[sc name=”ad_1″] QRLJacking or Quick Response Code Login Jacking is a simple social engineering attack vector capable of session hijacking...