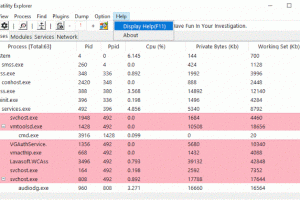
[sc name=”ad_1″] This program allows the user to access a Memory Dump. It can also function as a plugin to the Volatility Framework (). This...
Tag - Explorer
Topics
- Articles416
- Cryptography and Encryption32
- Exploitation Tools292
- Forensics Tools23
- Information Gathering254
- Man-In-The-Middle19
- Mobile Security19
- Network Tools73
- Password Attacks48
- Pentest Linux Distributions24
- Post Exploitation32
- Reporting Tools11
- Reverse Engineering44
- Security Tools99
- Shop5
- Stress Testing1
- System Administration92
- Video Tutorials74
- Vulnerability Analysis157
- Web Application Security56
- Wireless Attacks29