DET (is provided AS IS), is a proof of concept to perform Data Exfiltration using either single or multiple channel(s) at the same time. This is a Proof of...
Tag - Exploitation Tools
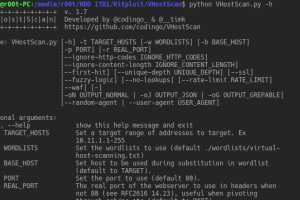
A virtual host scanner that can be used with pivot tools, detect catch-all scenarios, aliases and dynamic default pages. First presented at SecTalks BNE in...
Reverse Engineer .NET Assemblies dnSpy is a tool to reverse engineer .NET assemblies. It includes a decompiler, a debugger and an assembly editor (and more)...
The project is designed as a file resource cloner. Metadata, including digital signature, is extracted from one file and injected into another. Note: The...
Belati is tool for Collecting Public Data & Public Document from Website and other service for OSINT purpose. This tools is inspired by Foca and Datasploit...
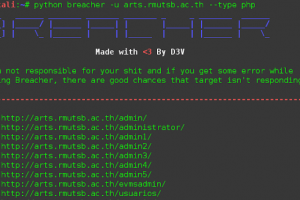
A script to find admin login pages and EAR vulnerabilites. Features Multi-threading on demand Big path list (798 paths) Supports php, asp and html extensions...
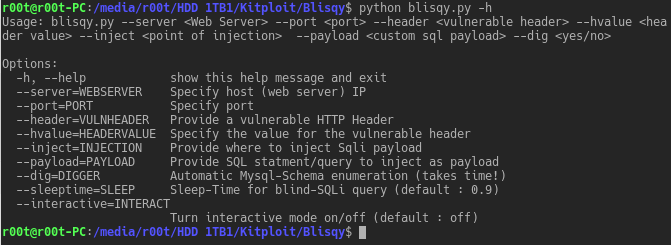
A slow data siphon for MySQL/MariaDB using bitwise operation on printable ASCII characters, via a blind-SQL injection. Usage USAGE: blisqy.py --server <Web...
AWSBucketDump is a tool to quickly enumerate AWS S3 buckets to look for loot. It’s similar to a subdomain bruteforcer but is made specifically for S3...
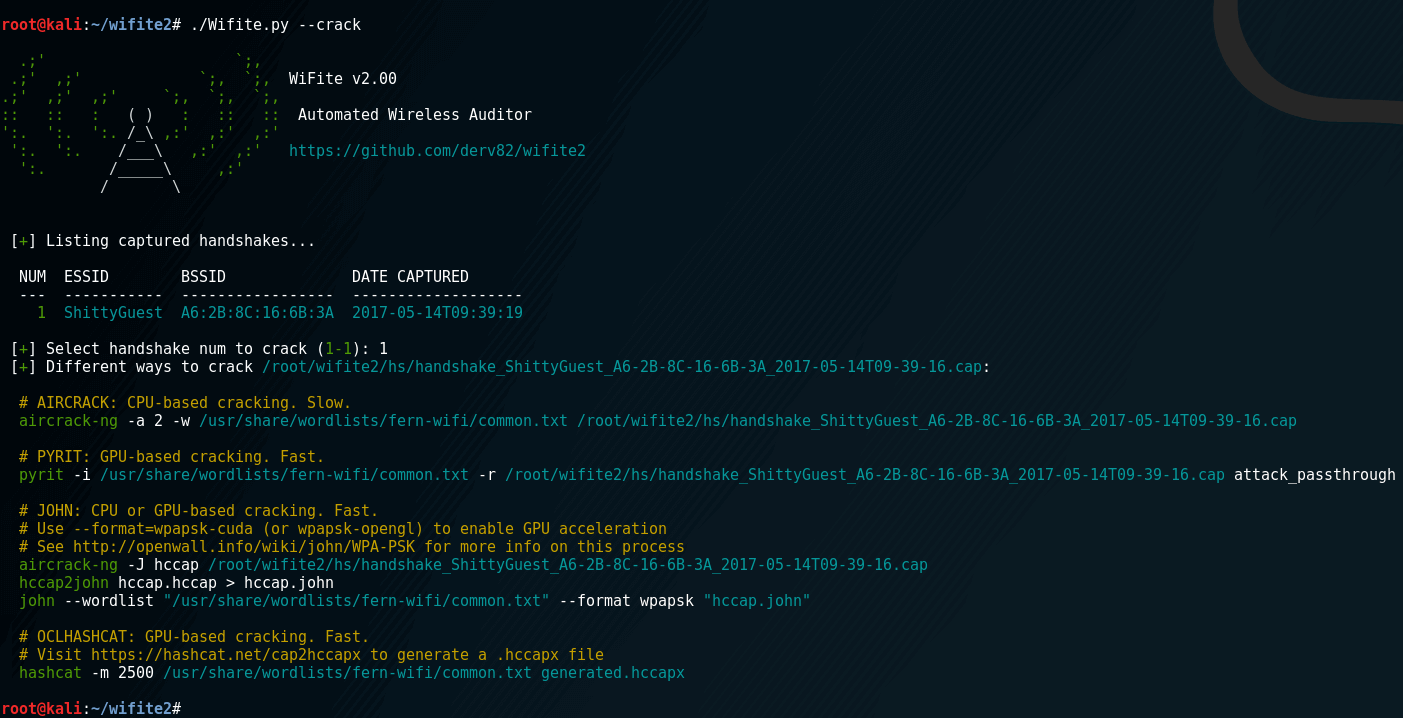
complete re-write of wifite, a Python script for auditing wireless networks. What’s new? Lots of files instead of “one big script”. Cleaner...
Portia aims to automate a number of techniques commonly performed on internal network penetration tests after a low privileged account has been compromised...