[sc name=”ad_1″] This is a proof of concept of how a ransomware works, and some techniques that we usually use to hijack our files. This project is...
Tag - Encryption
[sc name=”ad_1″] The program is designed to obfuscate the shellcode. Currently the tool supports 2 encryption. 1) XOR 2) AES The tool accepts...
[sc name=”ad_1″] Utility to find AES keys in running process memory. Works for 128, 192 and 256-bit keys. Usage Open aes-finder.sln solution in...
[sc name=”ad_1″] croc is a tool that allows any two computers to simply and securely transfer files and folders. AFAIK, croc is the only CLI file...
[sc name=”ad_1″] Tool for port forward & intranet proxy, just like lcx/ew, but better Why write? lcx and ew are awesome, but can be improved...
[sc name=”ad_1″] Please note: We take Vault’s security and our users’ trust very seriously. If you believe you have found a security...
NXcrypt is a polymorphic ‘python backdoors’ crypter written in python by Hadi Mene (h4d3s) . The output is fully undetectable. NXcrypt can inject...
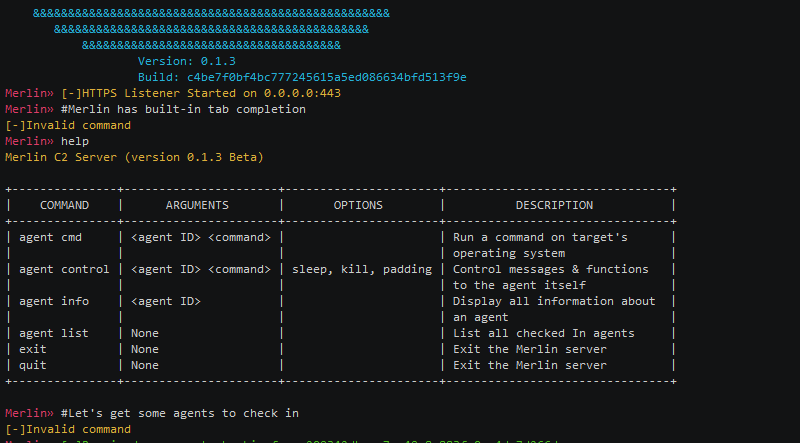
Merlin is a cross-platform post-exploitation framework that leverages HTTP/2 communications to evade inspection. HTTP/2 is a relatively new protocol that...
What this tool does is taking a file (any type of file), encrypt it, and embed it into an HTML file as ressource, along with an automatic download routine...
Forever 21 is investigating a potential data breach which may have compromised customer information and payment cards. On Tuesday, the US clothing retailer...