[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
Search Results For - iOS
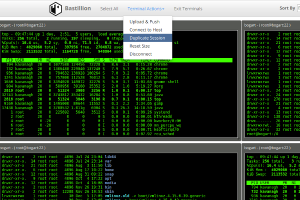
[sc name=”ad_1″] Bastillion is a web-based SSH console that centrally manages administrative access to systems. Web-based administration is...
[sc name=”ad_1″] Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk...
[sc name=”ad_1″] Git All the Payloads! A collection of web attack payloads. Pull requests are welcome! Usage run ./get.sh to download external...
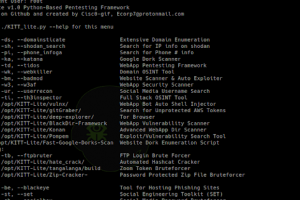
[sc name=”ad_1″] The KITT Penetration Testing Framework was developed as an open source solution for pentesters and programmers alike to compile...
[sc name=”ad_1″] There are many scenarios where you would want to recover deleted data from your Mac. These deleted files could be your important...
[sc name=”ad_1″] Prior to pandemic days, the restaurant industry talked of computers that might end up taking over their daily responsibilities...
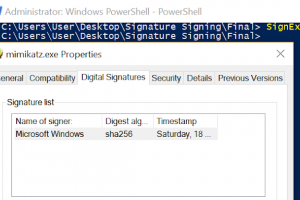
[sc name=”ad_1″] Hijacking legitimate digital signatures is a technique that can be used during red team assessments in order to sign PowerShell...
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
[sc name=”ad_1″] Runtime Mobile Security (RMS), powered by FRIDA, is a powerful web interface that helps you to manipulate Android Java Classes and...