The security vulnerability was discovered in the Linksys WVBR0-25 wireless video bridge, which was designed to enable the main Genie DVR to communicate over...
Search Results For - Wireless
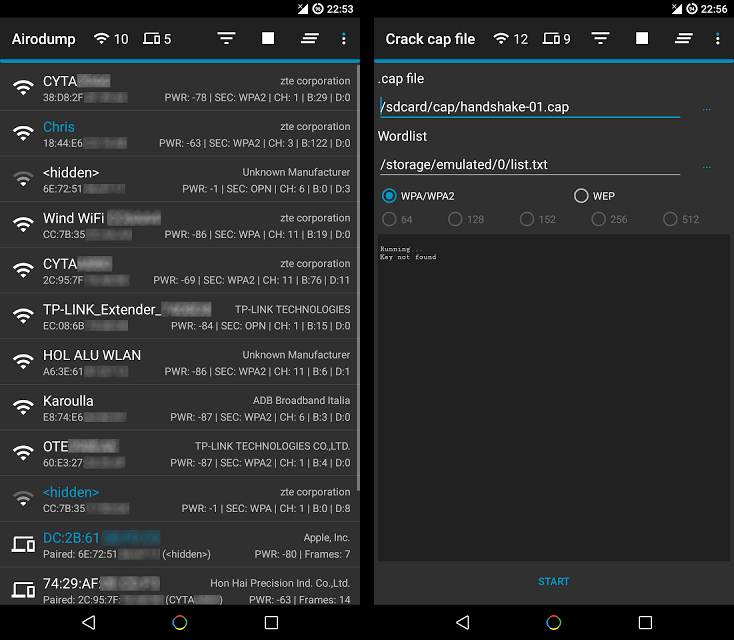
Hijacker is a Graphical User Interface for the penetration testing tools Aircrack-ng, Airodump-ng, MDK3 and Reaver. It offers a simple and easy UI to use these...
Kali Linux 2017.3 released, which includes all patches, fixes, updates, and improvements since our last release. In this release, the kernel has been updated...
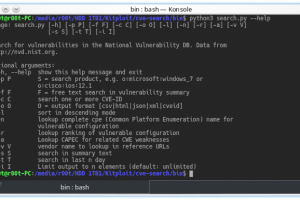
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Peterson now insists her father has been dismissed as a result of her video. In a mournful video, Peterson describes her father violated an Apple organization...
Just a year after Mirai—biggest IoT-based malware that caused vast Internet outages by launching massive DDoS attacks—completed its first anniversary, security...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
A convention in Athens, Greece, Munro detailed some of the appalling security lapses Pen Test Partners found while investigating naval ships that had things...
There is terrible news for all OnePlus lovers. Your OnePlus handset, running OxygenOS—the company’s custom version of the Android operating system, is...
A python program to create a fake AP and sniff data new in 2.0: SSLstrip2 for HSTS bypass Image capture with Driftnet TShark for command line .pcap capture...