[sc name=”ad_1″] Adobe is closing out this year with its December Patch Tuesday update to address a massive number of security vulnerabilities for...
Search Results For - Windows
[sc name=”ad_1″] Google, the FBI, ad-fraud fighting company WhiteOps and a collection of cyber security companies worked together to shut down one...
[sc name=”ad_1″] Cybersecurity researchers have discovered a new zero-day vulnerability in Adobe Flash Player that hackers are actively exploiting...
Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...
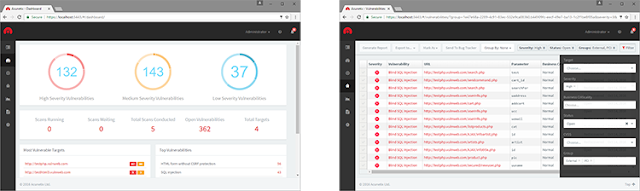
Acunetix, the pioneer in automated web application security software, has announced the release of Acunetix for Linux. Known to be reliable, cost-effective and...
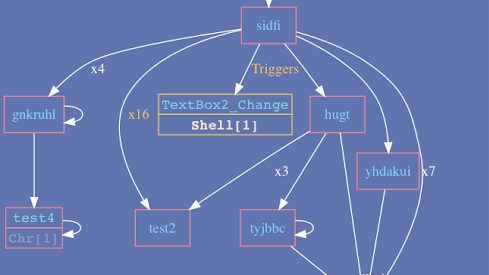
A tool for security researchers, who waste their time analyzing malicious Office macros. Generates a VBA call graph, with potential malicious keywords...
AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote...
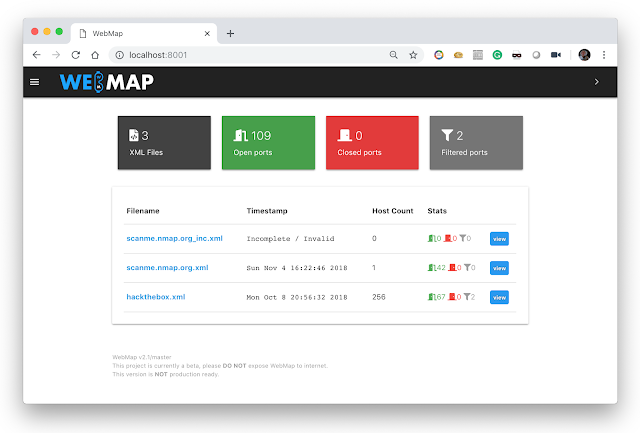
A Web Dashbord for Nmap XML Report Usage You should use this with docker, just by sending this command: $ mkdir /tmp/webmap $ docker run -d --name webmap -h...
Hide your powershell script in plain sight! Invisi-Shell bypasses all of Powershell security features (ScriptBlock logging, Module logging, Transcription...
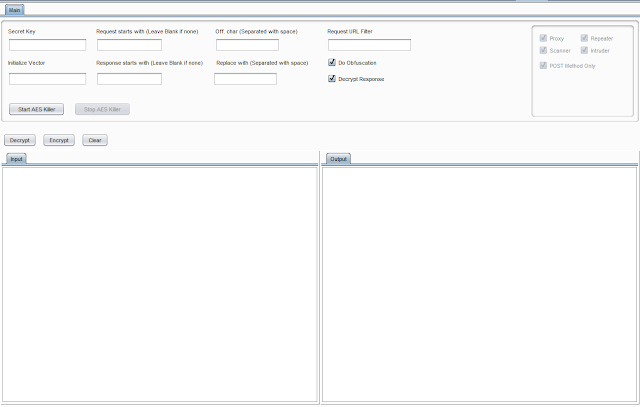
Burpsuite Plugin to decrypt AES Encrypted traffic on the fly. Requirements Burpsuite Java Tested on Burpsuite 1.7.36 Windows 10 xubuntu 18.04 Kali Linux 2018...