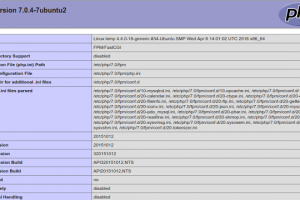
Check current PHP configuration for potential security flaws. Simply access this file from your webserver or run on CLI. Author This software was written by...
Search Results For - Vulnerable
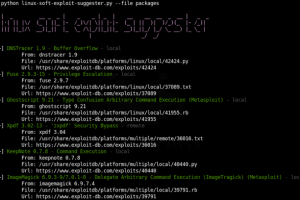
linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages...
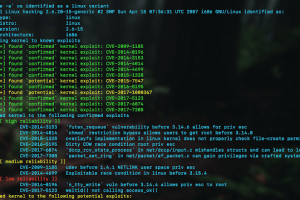
kernelpop is a framework for performing automated kernel exploit enumeration on Linux, Mac, and Windows hosts. Requirements python3 Currently supported...
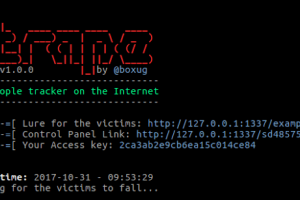
Trape is a recognition tool that allows you to track people, the information you can get is very detailed. We want to teach the world through this, as large...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
The British government has admitted publicly for the first time that it is all but certain North Korea carried out the “WannaCry” malware attack...
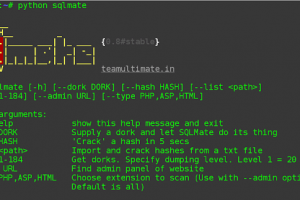
There are some features that we think SQLMap should have. Like finding admin panel of the target, better hash cracking etc. If you think the same, SQLMate is...
Burp Suite extension is able to find reflected XSS on page in real-time while browsing on web-site and include some features as: Highlighting of reflection in...
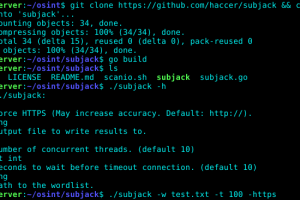
subjack is a Hostile Subdomain Takeover tool written in Go designed to scan a list of subdomains concurrently and identify ones that are able to be hijacked...