[sc name=”ad_1″] The United States Postal Service has patched a critical security vulnerability that exposed the data of more than 60 million...
Search Results For - Vulnerable
[sc name=”ad_1″] A widely used third-party NodeJS module with nearly 2 million downloads a week was compromised after one of its open-source...
[sc name=”ad_1″] This may sound crazy, but it’s true! The war for “most-subscribed Youtube channel” crown between T-Series and...
[sc name=”ad_1″] Developers around the world depend on open source components to build their software products. According to industry estimates...
Manticore is a symbolic execution tool for analysis of binaries and smart contracts. Note: Beginning with version 0.2.0, Python 3.6+ is required. Features...
Pacu is an open source AWS exploitation framework, designed for offensive security testing against cloud environments. Created and maintained by Rhino Security...
novahot is a webshell framework for penetration testers. It implements a JSON-based API that can communicate with trojans written in any language. By default...
Advanced search in search engines, enables analysis provided to exploit GET / POST capturing emails & urls, with an internal custom validation junction for...
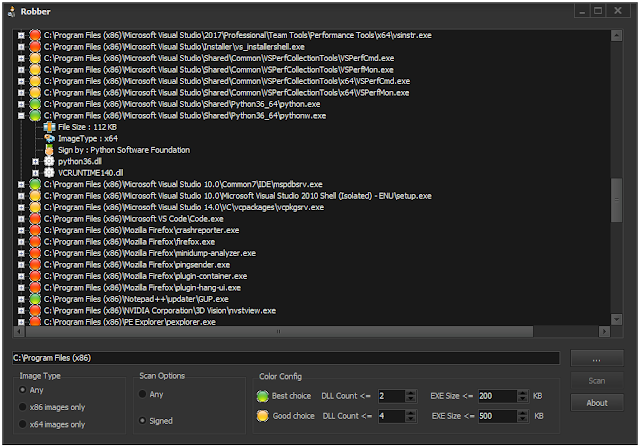
Robber is a free open source tool developed using Delphi XE2 without any 3rd party dependencies. What is DLL hijacking ?! Windows has a search path for DLLs in...
Tumblr today published a report admitting the presence of a security vulnerability in its website that could have allowed hackers to steal login credentials...