[sc name=”ad_1″] A new reminder for those who are still holding on to the Windows 7 operating system—you have one year left until Microsoft ends...
Search Results For - Vulnerable
[sc name=”ad_1″] Almost every activity on the Internet starts with a DNS query, a key function of the Internet that works as an Internet’s...
[sc name=”ad_1″] Security researchers have discovered three vulnerabilities in Systemd, a popular init system and service manager for most Linux...
[sc name=”ad_1″] Shodan is a search engine on the internet where you can find interesting things all over the world. For example, we can find...
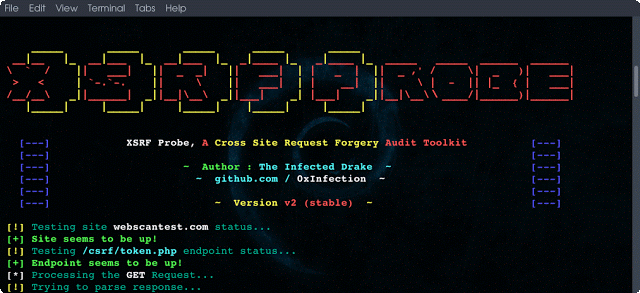
[sc name=”ad_1″] XSRFProbe is an advanced Cross Site Request Forgery (CSRF/XSRF) Audit and Exploitation Toolkit. Equipped with a Powerful Crawling...
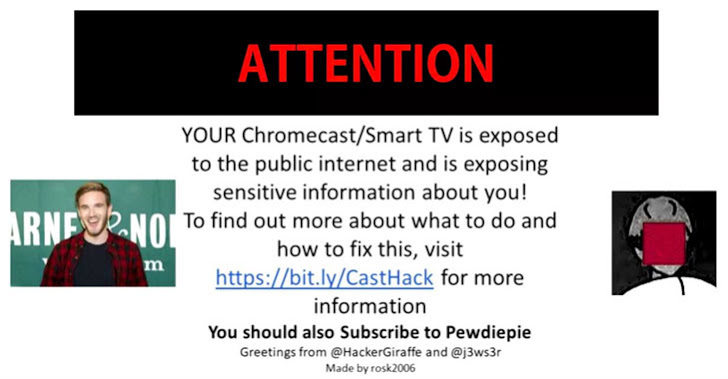
[sc name=”ad_1″] A group of hackers has hijacked tens of thousands of Google’s Chromecast streaming dongles, Google Home smart speakers and...
[sc name=”ad_1″] Google has finally patched a privacy vulnerability in its Chrome web browser for Android that exposes users’ device model...
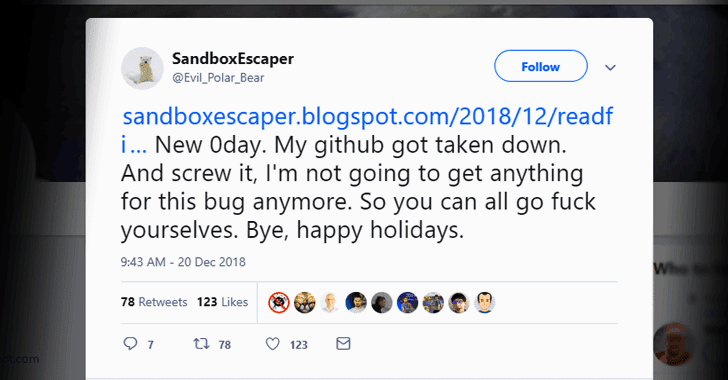
[sc name=”ad_1″] A security researcher with Twitter alias SandboxEscaper today released proof-of-concept (PoC) exploit for a new zero-day...
[sc name=”ad_1″] dawnscanner is a source code scanner designed to review your ruby code for security issues. dawnscanner is able to scan plain ruby...
[sc name=”ad_1″] Google today revealed that Google+ has suffered another massive data breach, forcing the tech giant to shut down its struggling...