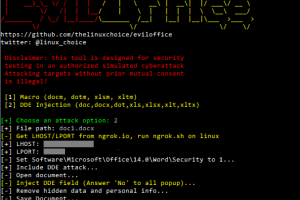
[sc name=”ad_1″] Win python script to inject Macro and DDE code into Excel and Word documents (reverse shell) Features: Inject malicious Macro on...
Search Results For - Tunneling
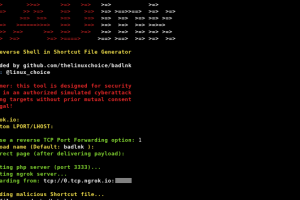
[sc name=”ad_1″] Reverse Shell in Shortcut File (.lnk) How it works? Shortcut file (Microsoft Windows 9.x) LNK is a file extension for a shortcut...
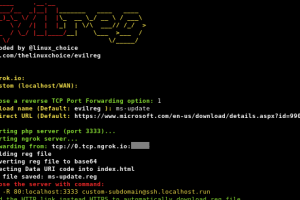
[sc name=”ad_1″] Reverse shell using Windows Registry file (.reg). Features: Reverse TCP Port Forwarding using Ngrok.io Requirements: Ngrok...
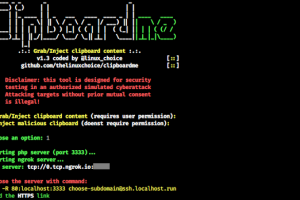
[sc name=”ad_1″] Grab/Inject Clipboard Content Browsers are implementing a new JavaScript API for asynchronous clipboard access to integrate copy...
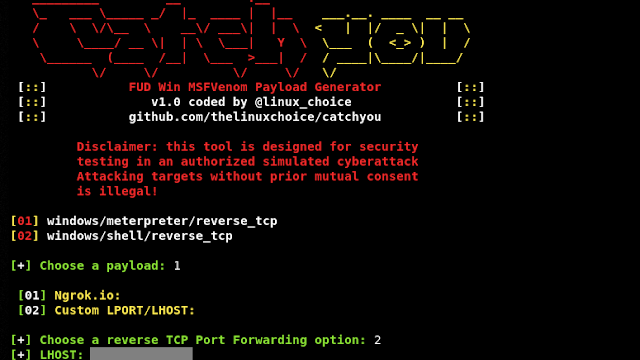
[sc name=”ad_1″] Fully Undetectable Win32 MSFVenom Payload Generator (meterpreter/shell reverse tcp) Author: github.com/thelinuxchoice/catchyou...
[sc name=”ad_1″] RITA is an open source framework for network traffic analysis. The framework ingests Bro/Zeek Logs in TSV format, and currently...
[sc name=”ad_1″] Lockdoor Framework : A Penetration Testing Framework With Cyber Security Resources. 09/2019 : 1.0Beta Information Gathring Tools...
[sc name=”ad_1″] Since most security tools also keep an eye on the network traffic to detect malicious IP addresses, attackers are increasingly...
Security researchers have discovered a serious code execution vulnerability in the LIVE555 streaming media library—which is being used by popular media...
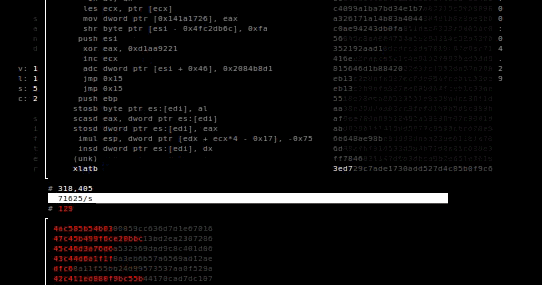
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...