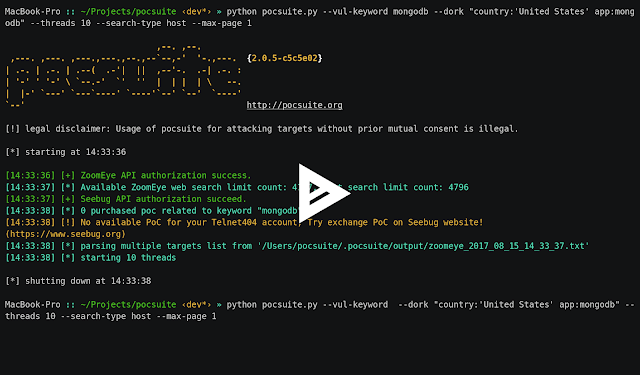
[sc name=”ad_1″] Pocsuite is an open-sourced remote vulnerability testing and proof-of-concept development framework developed by the Knownsec...
Search Results For - Tracking
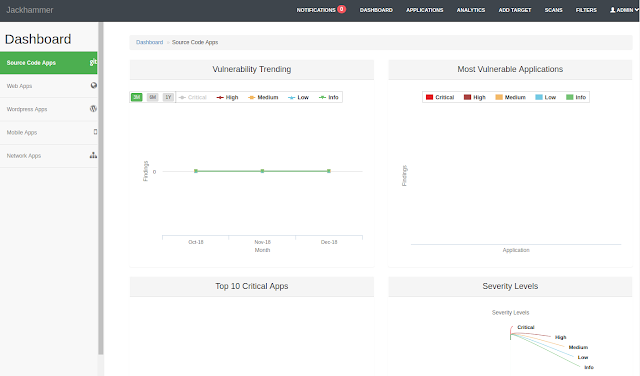
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...
[sc name=”ad_1″] It seems as though not a day goes by without a new story breaking about a high-level cyber attack on a major corporation or...
Pacu is an open source AWS exploitation framework, designed for offensive security testing against cloud environments. Created and maintained by Rhino Security...
Hey Guys, In this video i show you create your own private search engine using Searx. SearX: Installer Script: Searx is a free metasearch engine, available...
Hacking requires a lot of brainstorming since you need a robust machine that will not lag or run out of resources during working. Hacking involves DDOS a...
Raspberry Pi 3 Model B+ is now on sale for $35 (the same price as the existing Raspberry Pi 3 Model B), featuring: A 1.4GHz 64-bit quad-core ARM Cortex-A53 CPU...
FIDO U2F Security key is a personal encryption method which individualizes your online security by providing a secondary layer of encryption via the USB port...
[sc name=”ad_1″] Hacking a Wi-Fi network using Kali Linux needs a wireless card that support monitor mode and packet injection. Not all wireless...
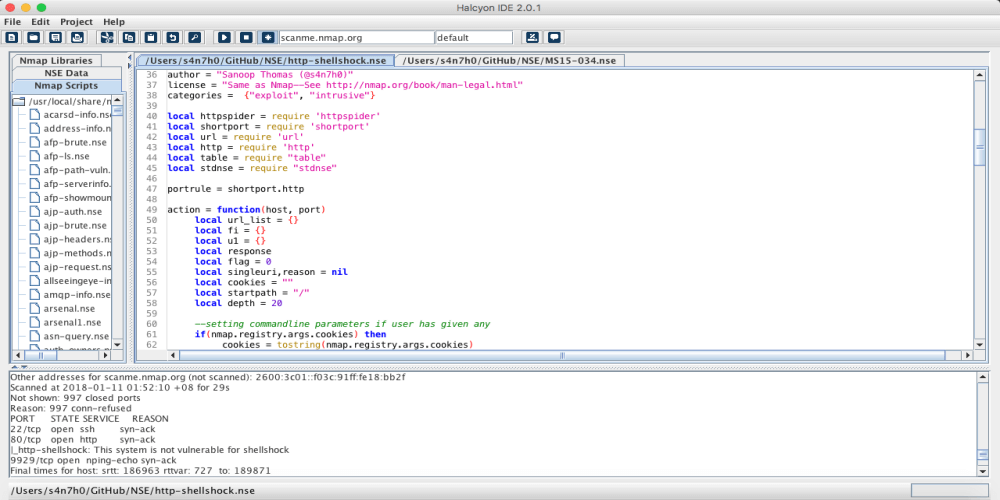
Halcyon IDE lets you quickly and easily develop scripts for performing advanced scans on applications and infrastructures with a range from recon to...