[sc name=”ad_1″] I hope you had biggest, happiest and craziest New Year celebration, but now it’s time to come back at work and immediately update...
Search Results For - Threat
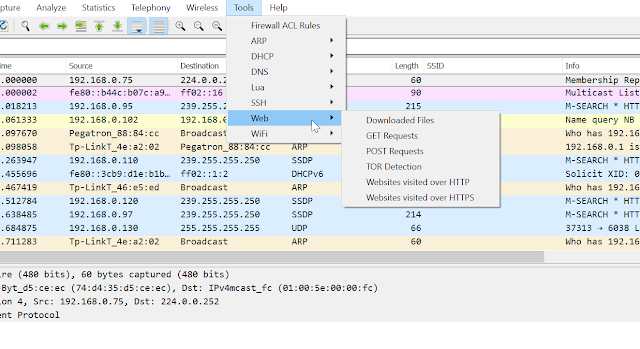
[sc name=”ad_1″] PA Toolkit is a collection of traffic analysis plugins to extend the functionality of Wireshark from a micro-analysis tool and...
[sc name=”ad_1″] The US Department of Justice on Thursday charged two Chinese hackers associated with the Chinese government for hacking numerous...
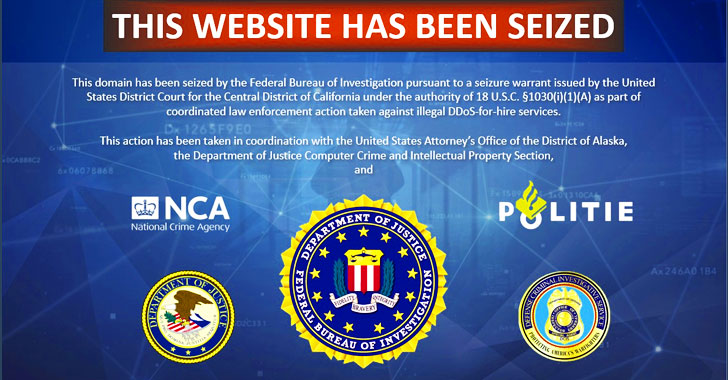
[sc name=”ad_1″] The FBI just saved the Christmas. The U.S. Justice Department announced earlier today that the FBI has seized domains of 15...
[sc name=”ad_1″] Microsoft today issued an out-of-band security update to patch a critical zero-day vulnerability in Internet Explorer (IE) Web...
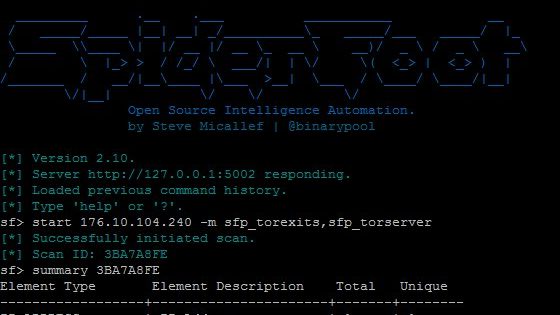
SpiderFoot is an open source intelligence (OSINT) automation tool. Its goal is to automate the process of gathering intelligence about a given target, which...
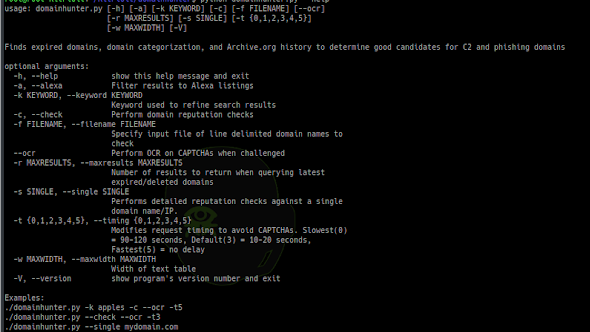
Domain name selection is an important aspect of preparation for penetration tests and especially Red Team engagements. Commonly, domains that were used...
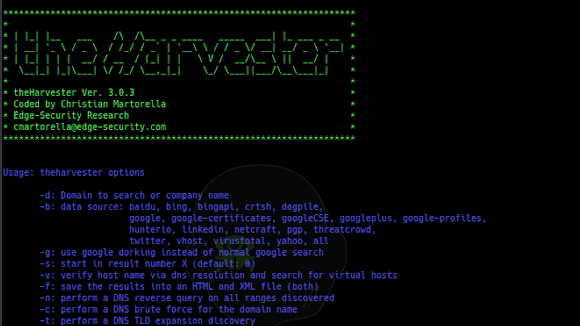
theHarvester is a tool for gathering subdomain names, e-mail addresses, virtual hosts, open ports/ banners, and employee names from different public sources...
[sc name=”ad_1″] The real identity of Tessa88—the notorious hacker tied to several high-profile cyber attacks including the LinkedIn, DropBox and...
[sc name=”ad_1″] Earlier this week Dropbox team unveiled details of three critical vulnerabilities in Apple macOS operating system, which...