[sc name=”ad_1″] Docker for pentest is an image with the more used tools to create an pentest environment easily and quickly. Features OS...
Search Results For - Takeover
[sc name=”ad_1″] The script aims to help in classifying vulnerabilities in web applications. The methodology RecoX is arising can spot weaknesses...
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
[sc name=”ad_1″] Lockdoor Framework : A Penetration Testing Framework With Cyber Security Resources. 09/2019 : 1.0Beta Information Gathring Tools...
[sc name=”ad_1″] This tool launches attack on k8s cluster from within. That means you already need to have an access with permission to deploy pods...
[sc name=”ad_1″] Exclusive — If you have not updated your website to the latest WordPress version 5.0.3, it’s a brilliant idea to upgrade the...
[sc name=”ad_1″] It’s 2019, and just clicking on a specially crafted URL would have allowed an attacker to hack your Facebook account without...
[sc name=”ad_1″] A security researcher has discovered multiple one-click client-side vulnerabilities in the some of the world’s most popular...
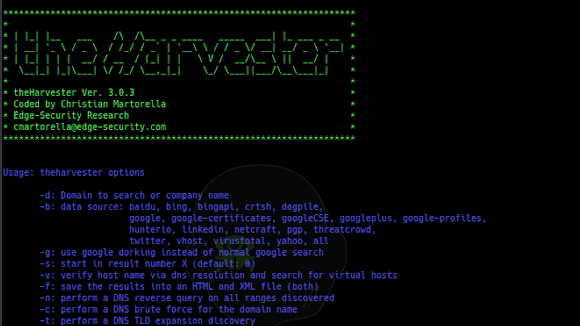
theHarvester is a tool for gathering subdomain names, e-mail addresses, virtual hosts, open ports/ banners, and employee names from different public sources...
[sc name=”ad_1″] The real identity of Tessa88—the notorious hacker tied to several high-profile cyber attacks including the LinkedIn, DropBox and...