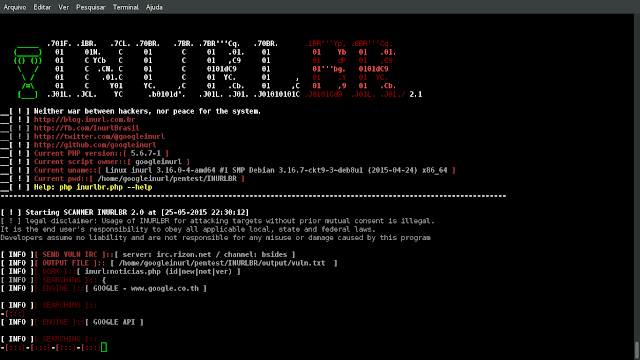
Advanced search in search engines, enables analysis provided to exploit GET / POST capturing emails & urls, with an internal custom validation junction for...
Search Results For - Shodan
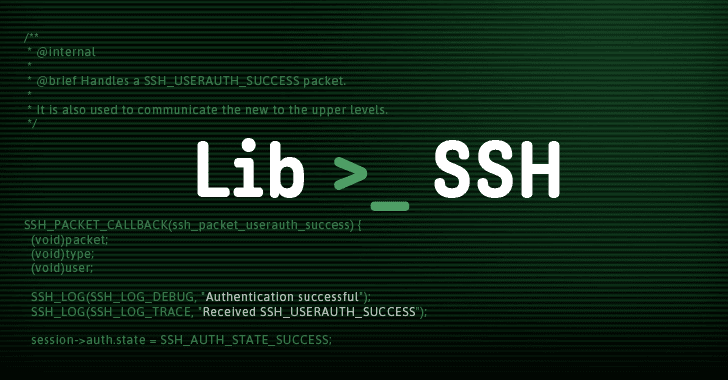
A four-year-old severe vulnerability has been discovered in the Secure Shell (SSH) implementation library known as Libssh that could allow anyone to completely...
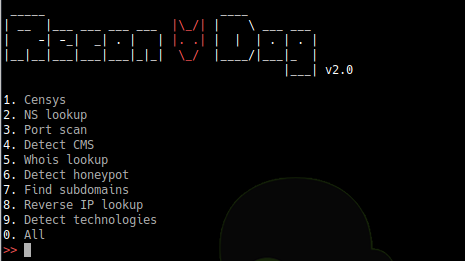
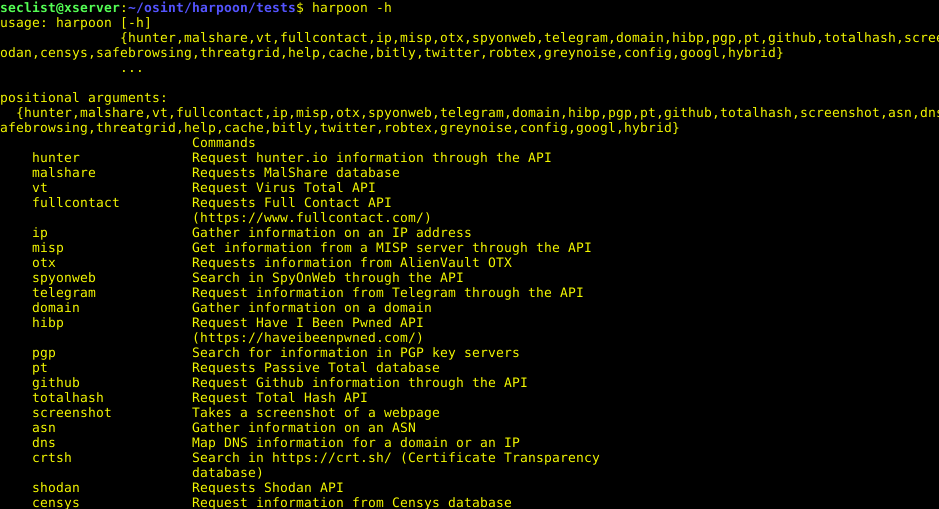
Reconnaissance Swiss Army Knife Main Features Wizard + CLA interface Can extracts targets from STDIN (piped input) and act upon them All the information is...
SubFinder is a subdomain discovery tool that discovers valid subdomains for websites by using passive online sources. It has a simple modular architecture and...
Red Team Arsenal is a web/network security scanner which has the capability to scan all company’s online facing assets and provide an holistic security view of...
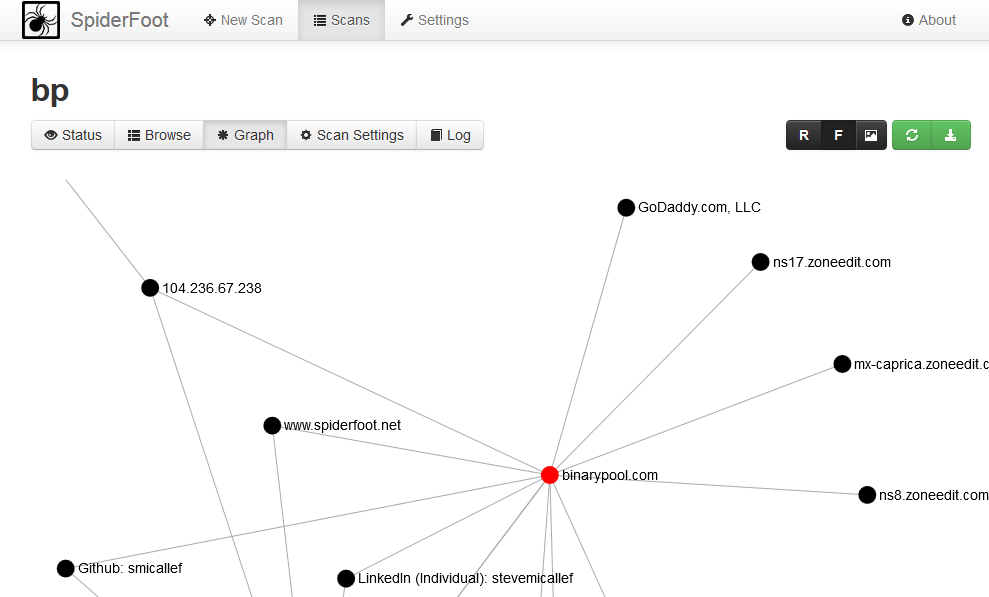
SpiderFoot is a reconnaissance tool that automatically queries over 100 public data sources (OSINT) to gather intelligence on IP addresses, domain names, e...
OSINT tool, CLI Tool For Open Source And Threat Intelligence Install You can simply pip install the tool: pip3 install git+ --process-dependency-links...
theHarvester is a tool for gathering e-mail accounts, subdomain names, virtual hosts, open ports/ banners, and employee names from different public sources...
As the name might suggest AutoSploit attempts to automate the exploitation of remote hosts. Targets are collected automatically as well by employing the Shodan...
gOSINT is a small OSINT framework in golang, it’s actually in development and still not ready for production if you want, feel free to contribute! What...