DUHK (Don’t Use Hard-coded Keys) is a new crypto implementation attack that could enable attackers to obtain secret keys that secure VPN (Virtual Private...
Search Results For - Sensitive Information
Multi-platform transparent client-side encryption of your files in the cloud. Cryptomator provides transparent, client-side encryption for your cloud. Protect...
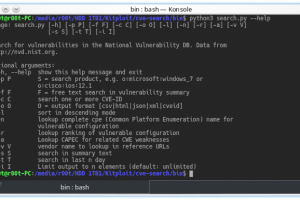
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
If you are an iPhone user and use Uber app, you would be surprised to know that widely popular ride-hailing app can record your screen secretly. Security...
It seems sophisticated hackers have changed the way they conduct targeted cyber operations—instead of investing in zero-days and developing their malware; some...