[sc name=”ad_1″] Pentest Cyber Range for a small Active Directory Domain. Automated templates for building your own Pentest/Red Team/Cyber Range in...
Search Results For - Secure
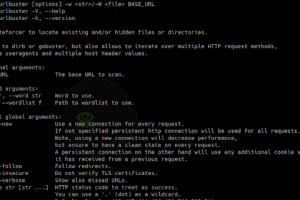
[sc name=”ad_1″] Powerful web directory fuzzer to locate existing and/or hidden files or directories. Similar to dirb or gobuster, but with a lot...
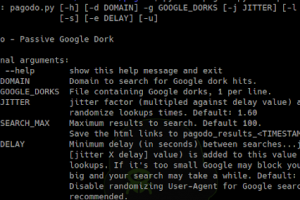
[sc name=”ad_1″] The goal of this project was to develop a passive Google dork script to collect potentially vulnerable web pages and applications...
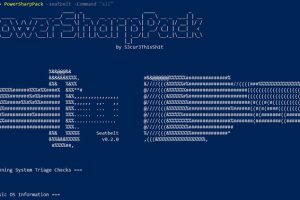
[sc name=”ad_1″] Many usefull offensive CSharp Projects wraped into Powershell for easy usage. Why? In my personal opinion offensive Powershell is...
[sc name=”ad_1″] Automated Instagram Unfollower Bot. Installation : apt update apt install git curl -y git clone git://github.com/htr-tech/unfollow...
[sc name=”ad_1″] Bastillion is a web-based SSH console that centrally manages administrative access to systems. Web-based administration is...
[sc name=”ad_1″] cnitch (snitch or container snitch) is a simple framework and command line tool for monitoring Docker containers to identify any...
[sc name=”ad_1″] Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk...
[sc name=”ad_1″] A graphical interface to use information security tools by the browser. Getting Started Kali Linux Tools Interface is a graphical...
[sc name=”ad_1″] Docker for pentest is an image with the more used tools to create an pentest environment easily and quickly. Features OS...