[sc name=”ad_1″] Magecart strikes again, one of the most notorious hacking groups specializes in stealing credit card details from poorly-secured e...
Search Results For - Secure Coding
[sc name=”ad_1″] A set of 36-year-old vulnerabilities has been uncovered in the Secure Copy Protocol (SCP) implementation of many client...
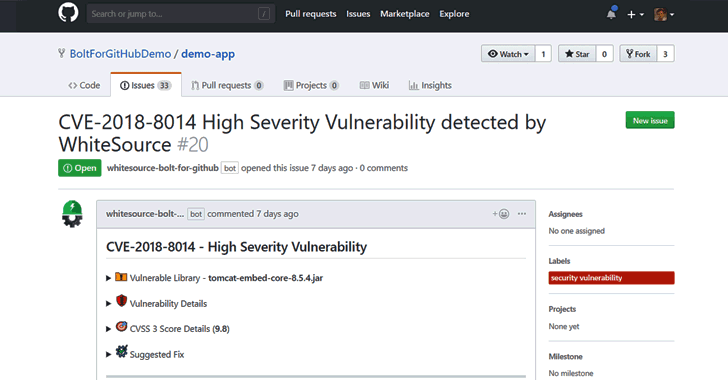
[sc name=”ad_1″] Developers around the world depend on open source components to build their software products. According to industry estimates...
A four-year-old severe vulnerability has been discovered in the Secure Shell (SSH) implementation library known as Libssh that could allow anyone to completely...
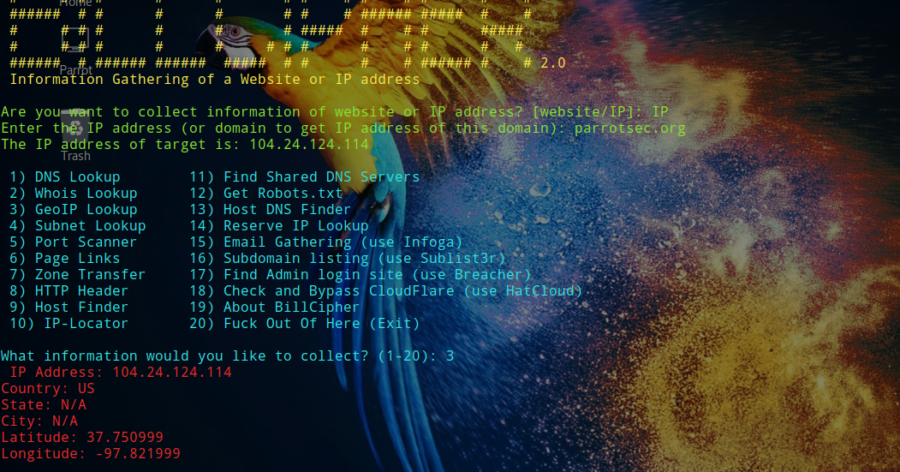
Information Gathering tool for a Website or IP address, use some ideas from Devploit. BillCipher can work in any operating system if they have and support...
Interview: Aragon’s Luis Cuende on Blockchain Governance & Digital Jurisdictions Author: Bennett Garner Bennett Garner: You’ve said “humans enforce...
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also...