[sc name=”ad_1″] A California-based Voice-Over-IP (VoIP) services provider VOIPO has accidentally left tens of gigabytes of its customer data...
Search Results For - Scan
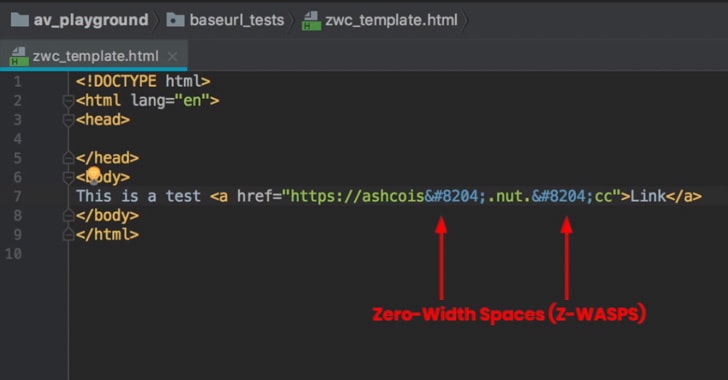
[sc name=”ad_1″] Security researchers have been warning about a simple technique that cybercriminals and email scammers are already being using in...
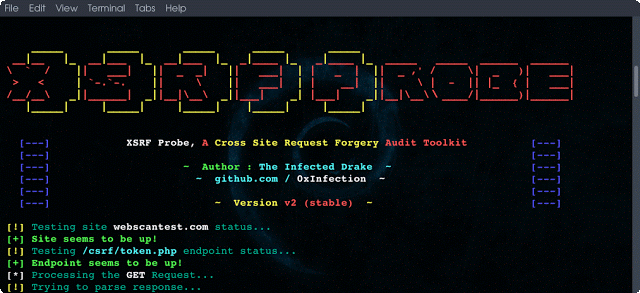
[sc name=”ad_1″] XSRFProbe is an advanced Cross Site Request Forgery (CSRF/XSRF) Audit and Exploitation Toolkit. Equipped with a Powerful Crawling...
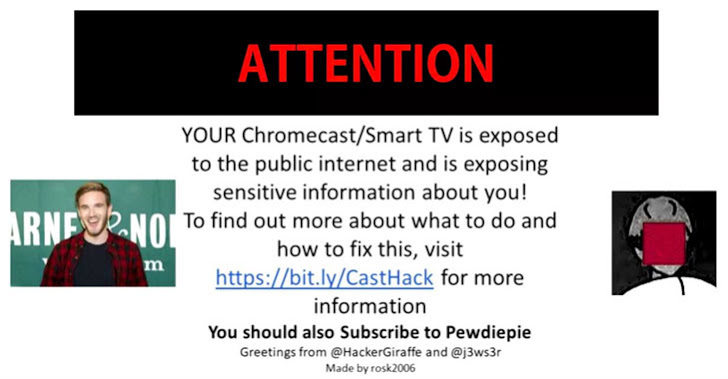
[sc name=”ad_1″] A group of hackers has hijacked tens of thousands of Google’s Chromecast streaming dongles, Google Home smart speakers and...
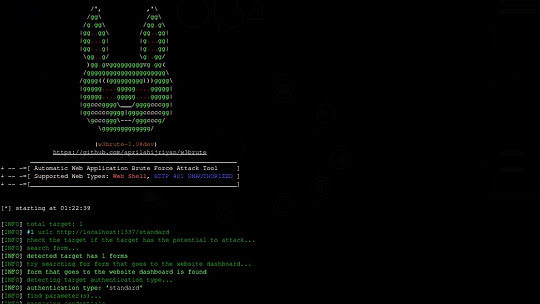
w3brute is an open source penetration testing tool that automates attacks directly to the website’s login page. w3brute is also supported for carrying...
[sc name=”ad_1″] Security researchers have discovered yet another example of how cybercriminals disguise their malware activities as regular...
[sc name=”ad_1″] Shamoon is back… one of the most destructive malware families that caused damage to Saudi Arabia’s largest oil producer in...
[sc name=”ad_1″] Facebook’s latest screw-up — a programming bug in Facebook website accidentally gave 1,500 third-party apps access to the...
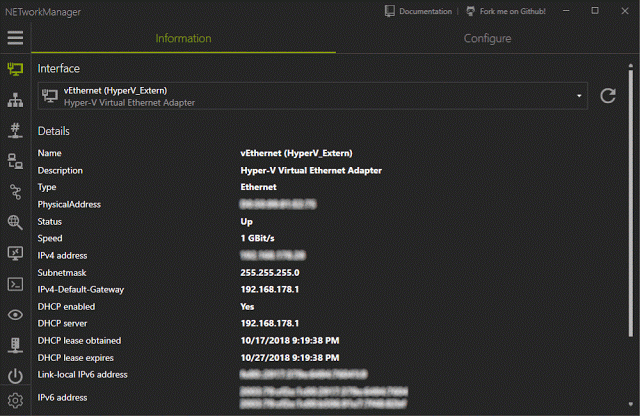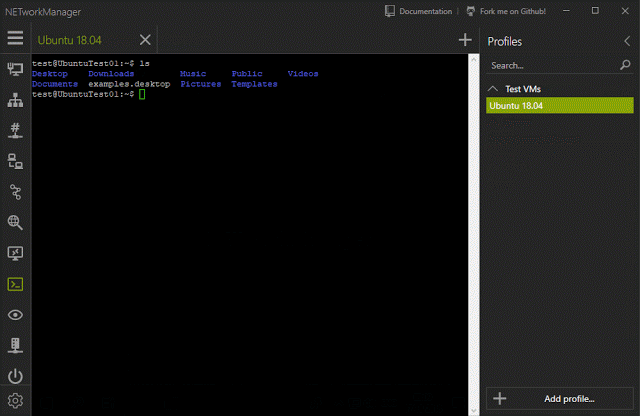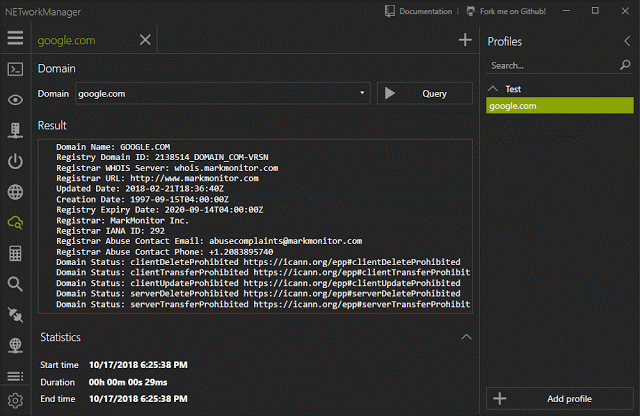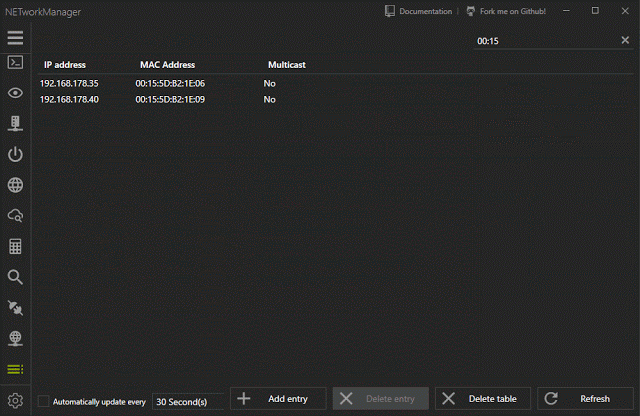
[sc name=”ad_1″] A powerful tool for managing networks and troubleshoot network problems! Features Network Interface – Information, Configure...
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...