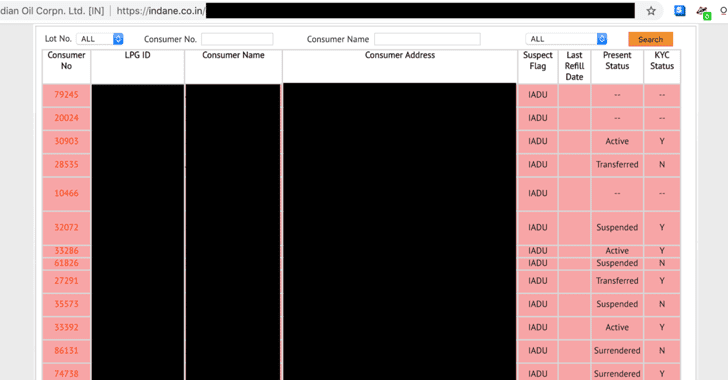
[sc name=”ad_1″] Why would someone bother to hack a so-called “ultra-secure encrypted database that is being protected behind 13 feet high...
Search Results For - Research
[sc name=”ad_1″] It’s 2019, and just clicking on a specially crafted URL would have allowed an attacker to hack your Facebook account without...
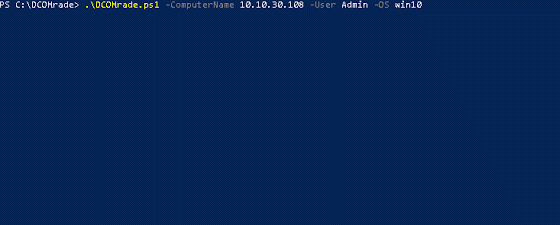
[sc name=”ad_1″] DCOMrade is a Powershell script that is able to enumerate the possible vulnerable DCOM applications that might allow for...
[sc name=”ad_1″] The United States Department of Justice has announced espionage charges against a former US Air Force intelligence officer with...
[sc name=”ad_1″] A serious security vulnerability has been discovered in the core runC container code that affects several open-source container...
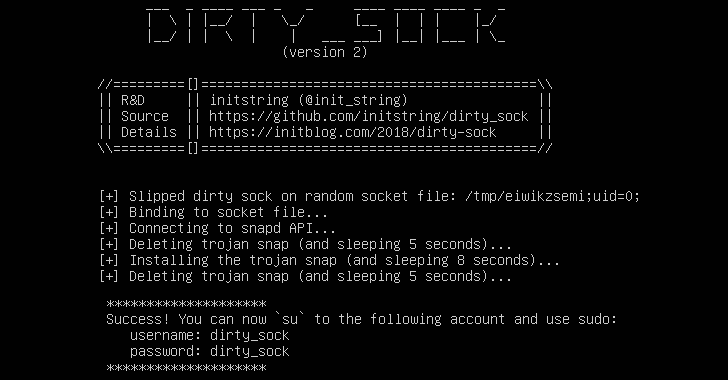
[sc name=”ad_1″] Ubuntu and some other Linux distributions suffer from a severe privilege escalation vulnerability that could allow a local...
[sc name=”ad_1″] A new security vulnerability has been discovered in the latest version of Apple’s macOS Mojave that could allow a malicious...
[sc name=”ad_1″] Smart devices definitely make our lives easier, faster, and more efficient, but unfortunately, an insecure smart device can also...
[sc name=”ad_1″] A malicious Windows EXE file can even infect your Mac computer as well. Yes, you heard me right — a .exe malware on macOS...
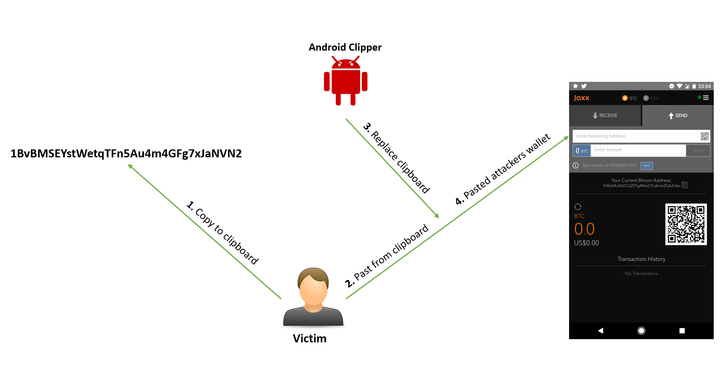
[sc name=”ad_1″] A security researcher has discovered yet another cryptocurrency-stealing malware on the official Google Play Store that was...