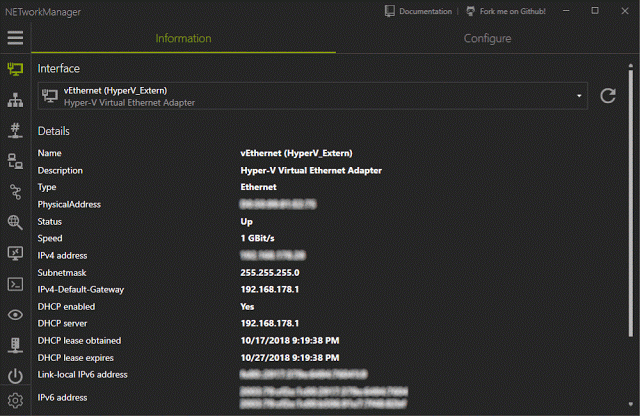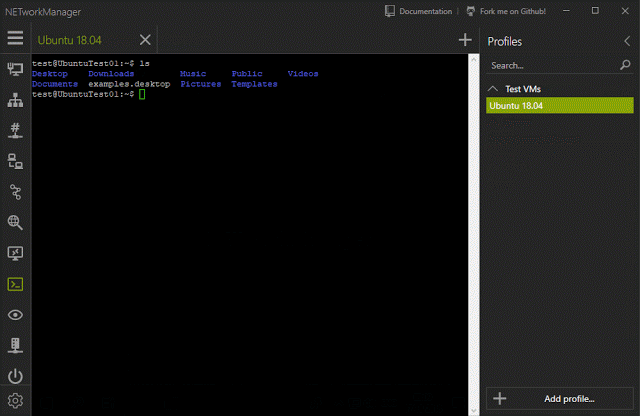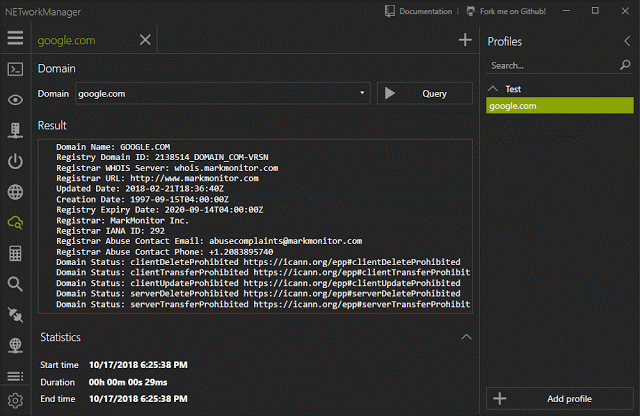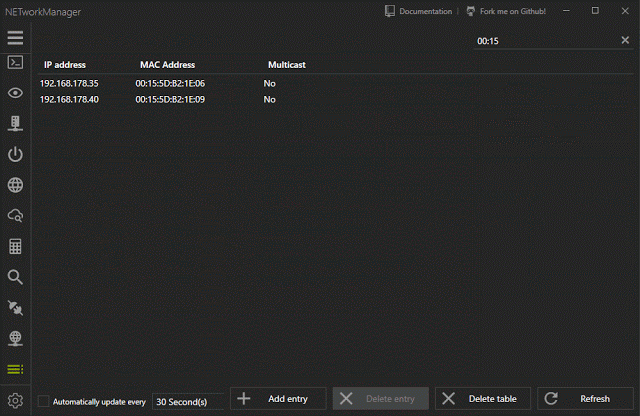
[sc name=”ad_1″] A powerful tool for managing networks and troubleshoot network problems! Features Network Interface – Information, Configure...
Search Results For - Requirements
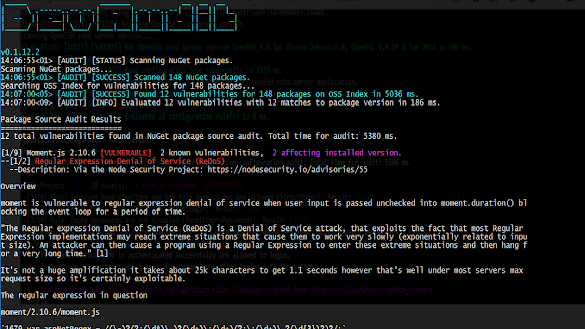
[sc name=”ad_1″] DevAudit is an open-source, cross-platform, multi-purpose security auditing tool targeted at developers and teams adopting DevOps...
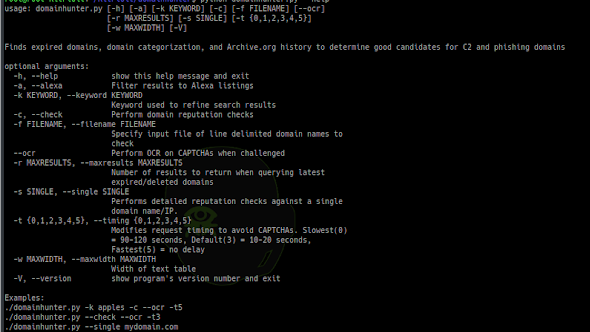
Domain name selection is an important aspect of preparation for penetration tests and especially Red Team engagements. Commonly, domains that were used...
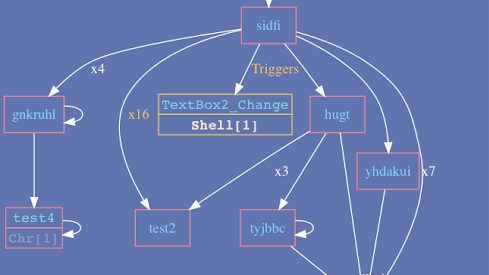
A tool for security researchers, who waste their time analyzing malicious Office macros. Generates a VBA call graph, with potential malicious keywords...
Manticore is a symbolic execution tool for analysis of binaries and smart contracts. Note: Beginning with version 0.2.0, Python 3.6+ is required. Features...
AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote...
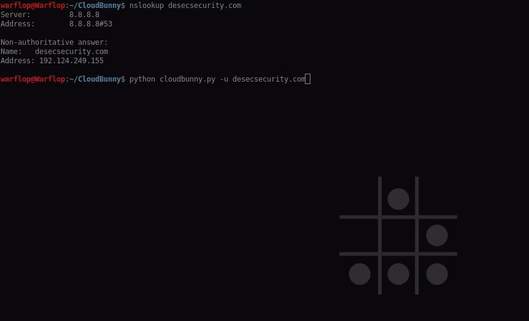
CloudBunny is a tool to capture the real IP of the server that uses a WAF as a proxy or protection. How works In this tool we used three search engines to...
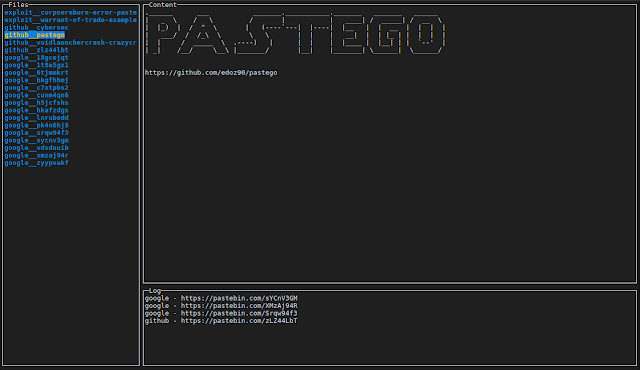
Scrape/Parse Pastebin using GO and grammar expression (PEG). Installation $ go get -u github.com/edoz90/pastego Usage Search keywords are case sensitive...
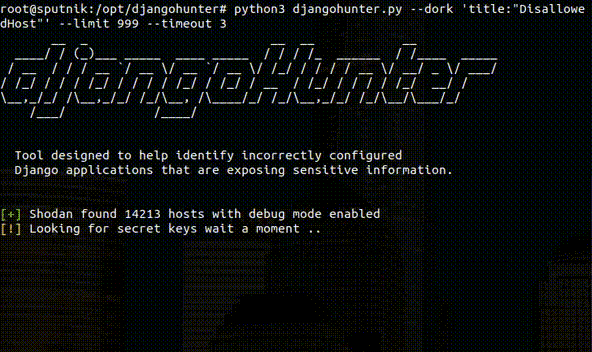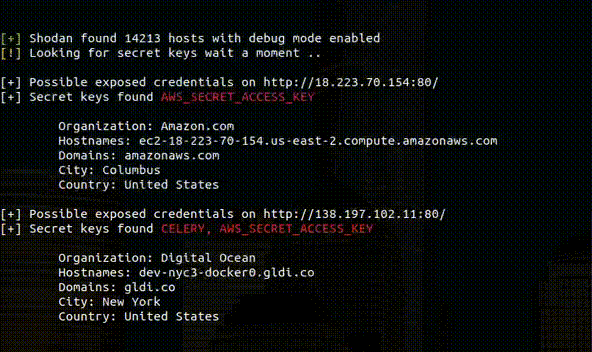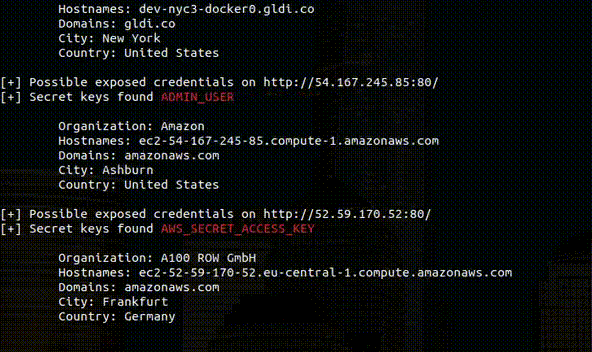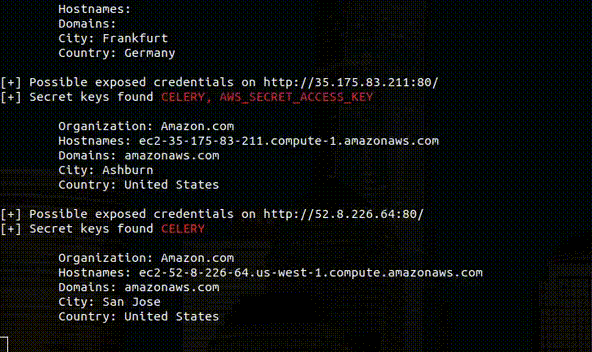
Tool designed to help identify incorrectly configured Django applications that are exposing sensitive information. Usage Usage: python3 djangohunter.py --key...
This tool allows you to perform OSINT and reconnaissance on an organisation or an individual. It allows one to search 1.4 Billion clear text credentials which...