[sc name=”ad_1″] Just in time… Cybersecurity experts this week fighting over Twitter in favor of not using HTTPS and suggesting software developers...
Search Results For - Repositories
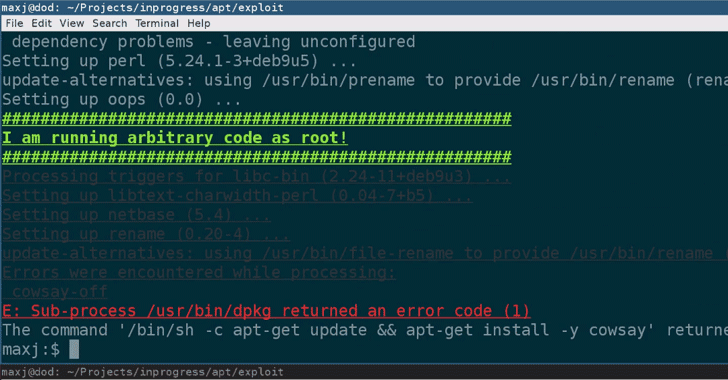
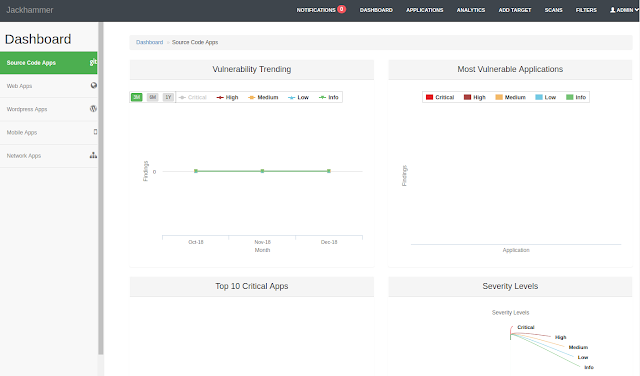
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...
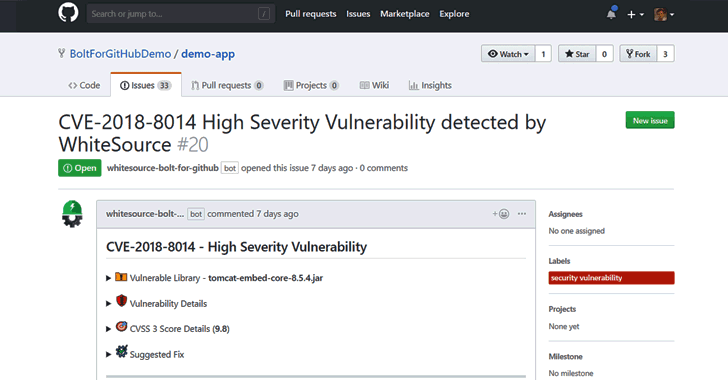
[sc name=”ad_1″] Developers around the world depend on open source components to build their software products. According to industry estimates...
This is the fourth and final release of 2018, This release brings the kernel up to version 4.18.10, fixes numerous bugs, includes many updated packages, and a...
Welcome to our fourth and final release of 2018, Kali Linux 2018.4, which is available for immediate download. This release brings kernel up to version 4.18...
TLS-Scanner is a tool created by the Chair for Network and Data Security from the Ruhr-University Bochum to assist pentesters and security researchers in the...
Security Monkey monitors your AWS and GCP accounts for policy changes and alerts on insecure configurations. Support is available for OpenStack public and...
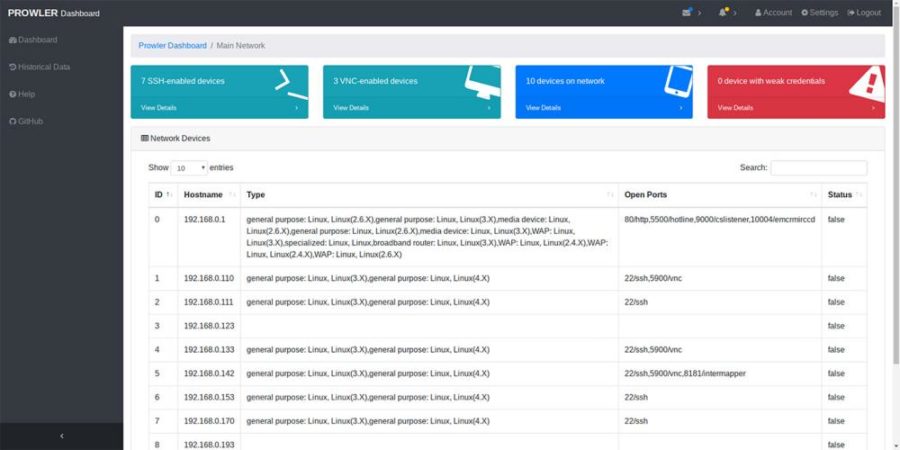
Prowler is a Network Vulnerability Scanner implemented on a Raspberry Pi Cluster, first developed during Singapore Infosec Community Hackathon – HackSmith v1.0...
SPARTA is a python GUI application which simplifies network infrastructure penetration testing by aiding the penetration tester in the scanning and enumeration...
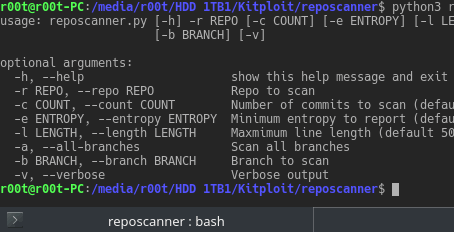
Reposcanner is a python script to search through the commit history of Git repositories looking for interesting strings such as API keys, inspires...