News of the event was posted on Twitter by vigilante hacker, “The Jester,” who has in the past increased fame by hacking jihadist websites, and who in October...
Search Results For - Reporting
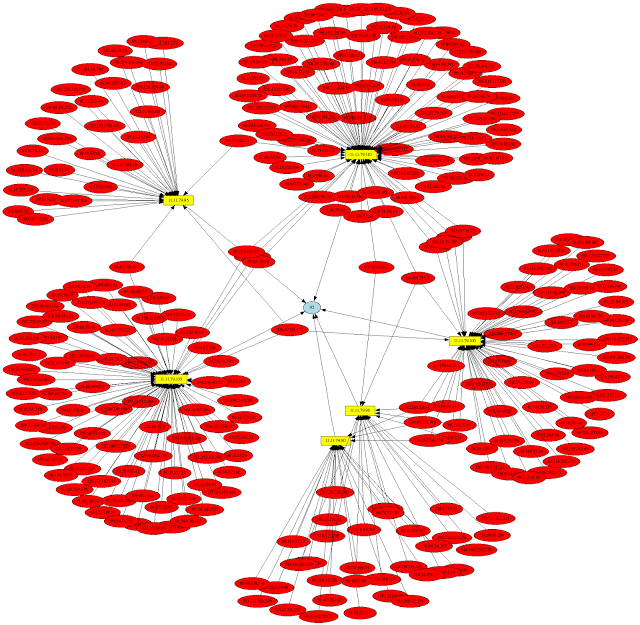
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
objection is a runtime mobile exploration toolkit, powered by Frida. It was built with the aim of helping assess mobile applications and their security posture...
A newly discovered unpatched attacking method that exploits a built-in feature of Microsoft Office is currently being used in various widespread malware attack...
The Port Scan Attack Detector psad is a lightweight system daemon written in is designed to work with Linux iptables/ip6tables/firewalld firewalling code to...
If you’re one of the users Facebook has decided to participate in the test, you’ll see this small button in the upper right-hand corner above an article’s...
Vanquish is a Kali Linux based Enumeration Orchestrator built in Python. Vanquish leverages the opensource enumeration tools on Kali to perform multiple active...
Do you know—United States Government has banned federal agencies from using Kaspersky antivirus software over spying fear? Though there’s no solid...