[sc name=”ad_1″] Exclusive — If you have not updated your website to the latest WordPress version 5.0.3, it’s a brilliant idea to upgrade the...
Search Results For - Red Team
[sc name=”ad_1″] Late last year when an unknown group of hackers stole secret access tokens for millions of Facebook accounts by taking advantage...
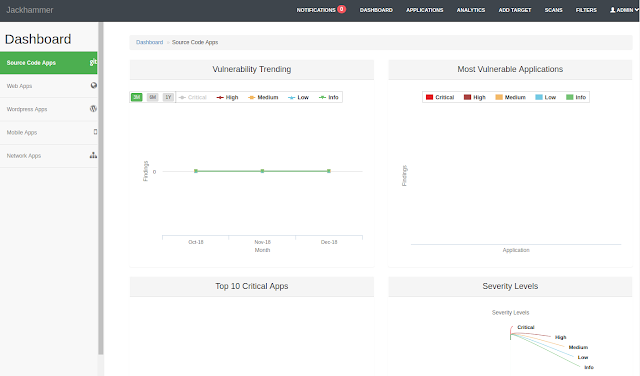
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...
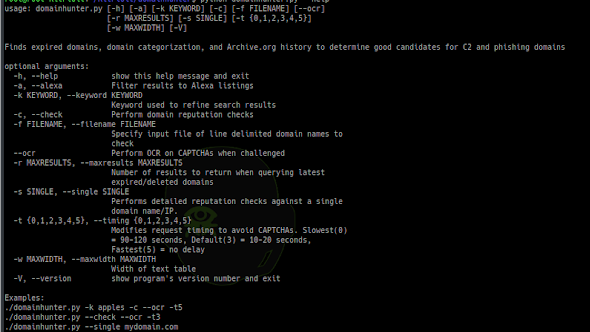
Domain name selection is an important aspect of preparation for penetration tests and especially Red Team engagements. Commonly, domains that were used...
[sc name=”ad_1″] This is why you should always think twice before opening innocent looking email attachments, especially word and pdf files...
Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...
It’s been quite a year for the open source platforms. Earlier this year, Microsoft acquired popular code repository hosting service GitHub for $7.5...
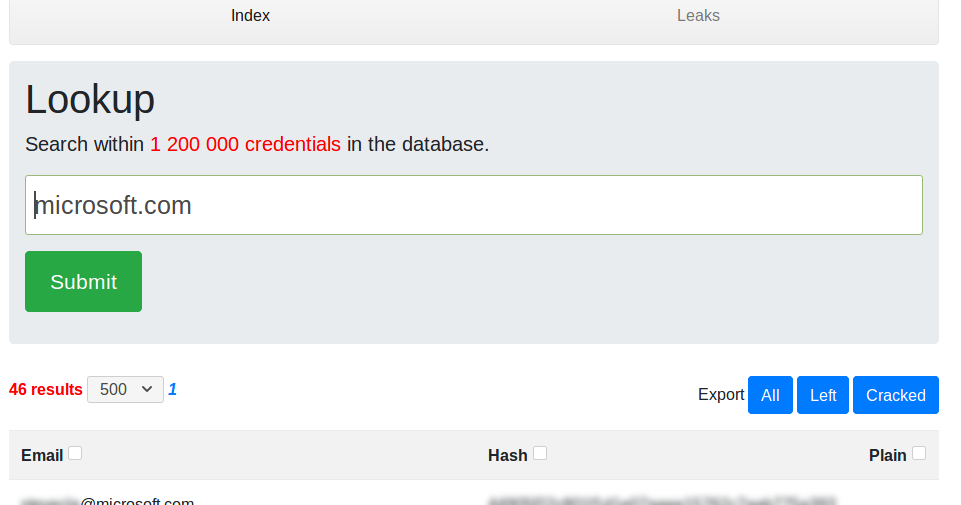
LeakScraper is an efficient set of tools to process and visualize huge text files containing credentials. These tools are designed to help...
Virtual Machine for Adversary Emulation and Threat Hunting RedHunt aims to be a one stop shop for all your threat emulation and threat hunting needs by...
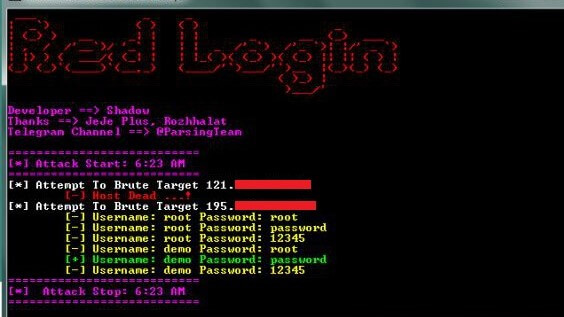
Red Login: SSH Brute-force Tools. Features: High speed and precision CLI ( Console based ) Run the arbitrary command after the attack is successful ( Default...