Break the ice with that cute Active Directory environment over there. Automates network attacks against Active Directory to deliver you piping hot plaintext...
Search Results For - PowerShell
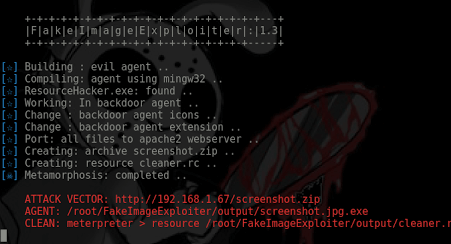
This module takes one existing image.jpg and one payload.ps1 (input by user) and builds a new payload (agent.jpg.exe) that if executed it will trigger the...
The Automated Collection and Enrichment (ACE) platform is a suite of tools for threat hunters to collect data from many endpoints in a network and...
DNSExfiltrator allows for transfering (exfiltrate) a file over a DNS request covert channel. This is basically a data leak testing tool allowing to exfiltrate...
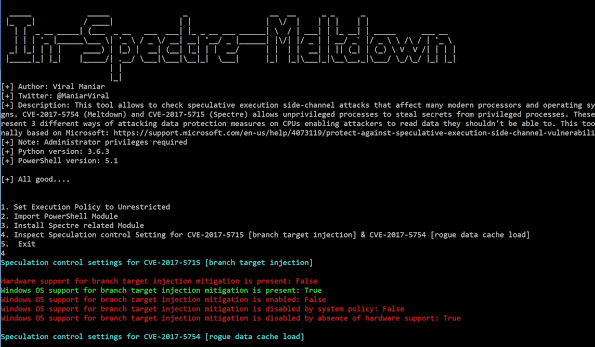
This tool allows to check speculative execution side-channel attacks that affect many modern processors and operating systems designs. CVE-2017-5754 (Meltdown)...
Invoke-MacroCreator is a powershell Cmdlet that allows for the creation of an MS-Word document embedding a VBA macro with various payload delivery and...
ADRecon is a tool which extracts various artifacts (as highlighted below) out of an AD environment in a specially formatted Microsoft Excel report that...
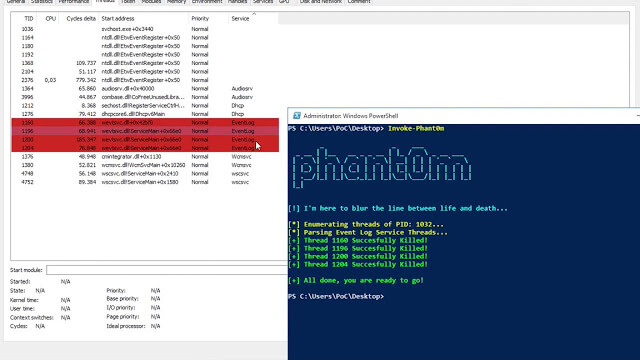
This script walks thread stacks of Event Log Service process (spesific svchost.exe) and identify Event Log Threads to kill Event Log Service Threads. So the...
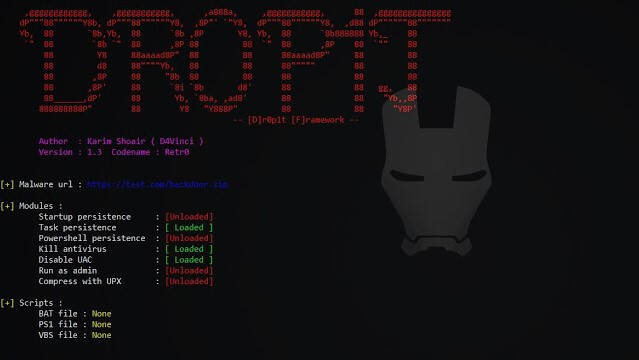
Have you ever heard about trojan droppers ? In short dropper is type of malware that downloads other malwares and Dr0p1t gives you the chance to create a...
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...