[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
Search Results For - Pentesting
[sc name=”ad_1″] FOCA (Fingerprinting Organizations with Collected Archives) FOCA is a tool used mainly to find metadata and hidden information in...
[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting...
[sc name=”ad_1″] If the connectivity and security of your organization rely on Cisco RV320 or RV325 Dual Gigabit WAN VPN routers, then you need to...
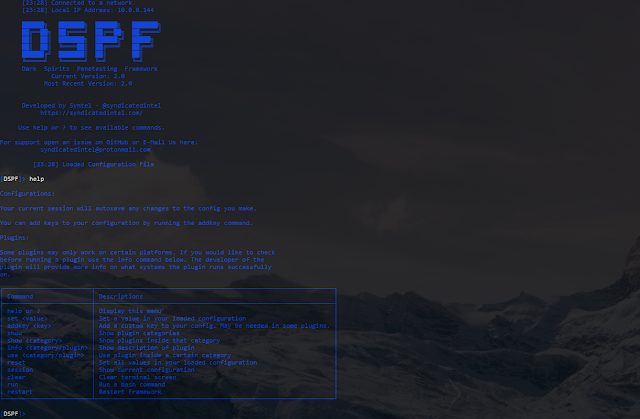
A penetration testing framework for Linux and Windows systems. What is DarkSpiritz? Created by the SynTel Team it was a project of one of the owners to update...
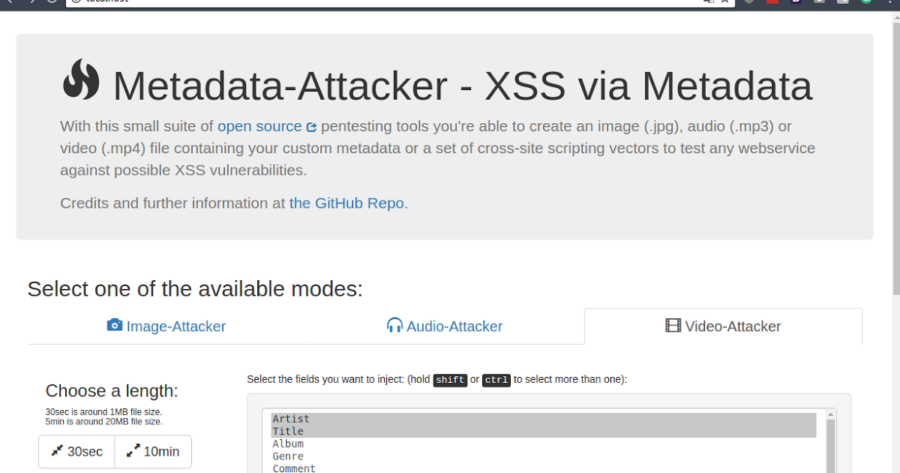
Metadata-Attacker or a set of cross-site scripting vectors to test any webservice against possible XSS vulnerabilities when displaying unfiltered meta datWith...
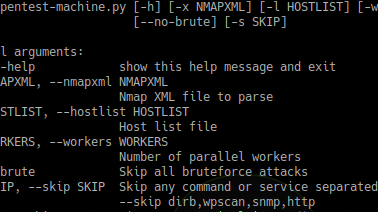
Automates some pentesting work via an nmap XML file. As soon as each command finishes it writes its output to the terminal and the files in output-by-service/...
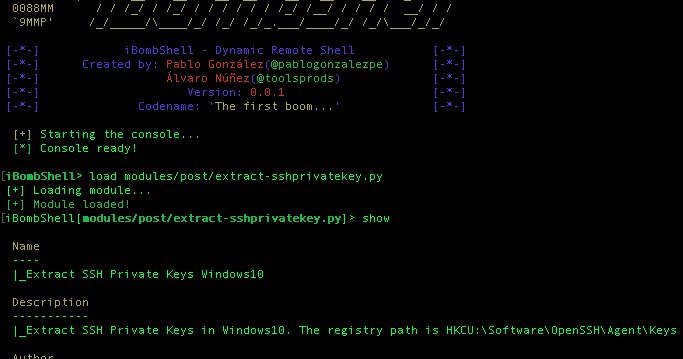
ibombshell is a tool written in Powershell that allows you to have a prompt at any time with post-exploitation functionalities (and in some cases exploitation)...
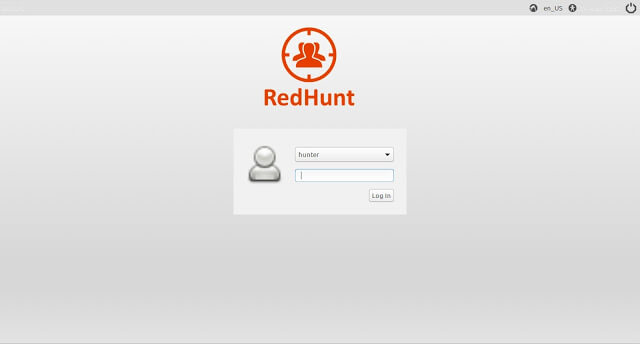
Virtual Machine for Adversary Emulation and Threat Hunting RedHunt aims to be a one stop shop for all your threat emulation and threat hunting needs by...
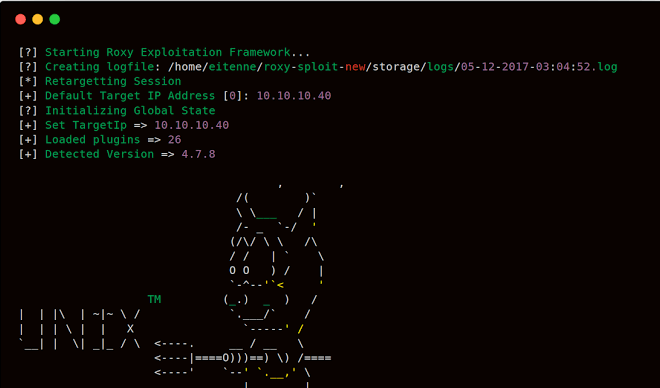
roxysploit is a community-supported, open-source and penetration testing suite that supports attacks for numerous scenarios. conducting attacks in the field...