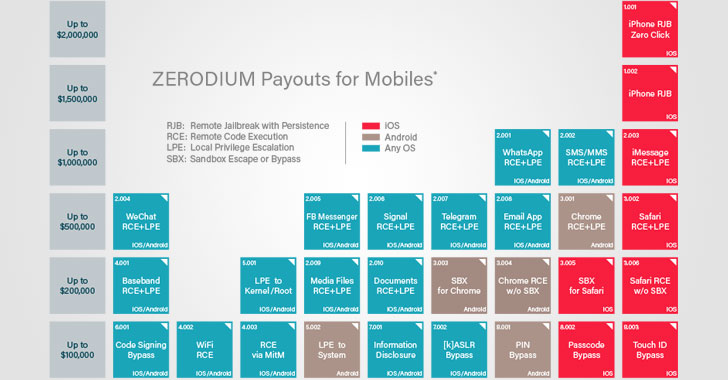
[sc name=”ad_1″] Well, there’s some good news for hackers and vulnerability hunters, though terrible news for tech manufacturers! Exploit...
Search Results For - Mobile App
[sc name=”ad_1″] Google has finally patched a privacy vulnerability in its Chrome web browser for Android that exposes users’ device model...
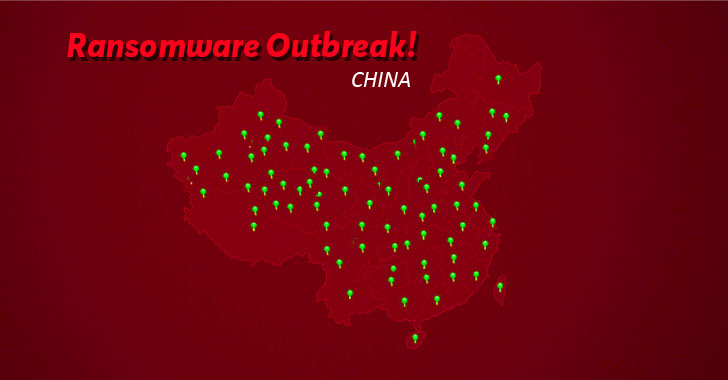
A new piece of ransomware is spreading rapidly across China that has already infected more than 100,000 computers in the last four days as a result of a supply...
A security enthusiast who discovered a passcode bypass vulnerability in Apple’s iOS 12 late last month has now dropped another passcode bypass bug that...
Nameles provides an easy to deploy, scalable IVT detection and filtering solution that is proven to detect at a high level of accuracy ad fraud and other types...
Author: Marshall Taylor Blockchains and their cryptocurrencies are energetically following a path similar to other major leaps in technology that have come...
Hacking requires a lot of brainstorming since you need a robust machine that will not lag or run out of resources during working. Hacking involves DDOS a...
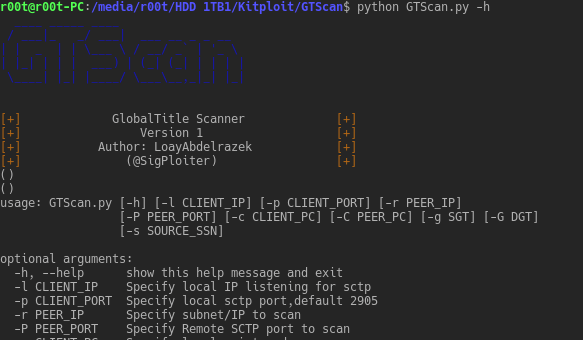
The Nmap Scanner for Telco. With the current focus on telecom security, there used tools in day to day IT side penetration testing should be extended to...
A security researcher (@s1guza) has published the details of an unpatched vulnerability in macOS that can be exploited to gain full control of a system. The...
Alphonso, a startup that retails media-viewing data, provides a plugin that listens for audio signals in shows and movies. Approximately 250 mobile...