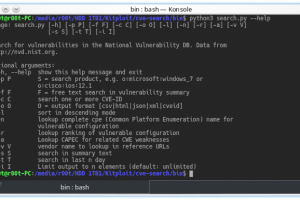
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Search Results For - Microsoft
To comply with the law, the DPA states that Microsoft requires getting valid user consent this indicates the company must be open about what data is gathered...
Rather than heavily protecting backdoors with hardcore packers, many malware authors evade heuristic detections by obfuscating only key portions of an...
The Qatar administration also told internet users that they would be reviewing the issue though no decision or official comment on the blocks themselves have...
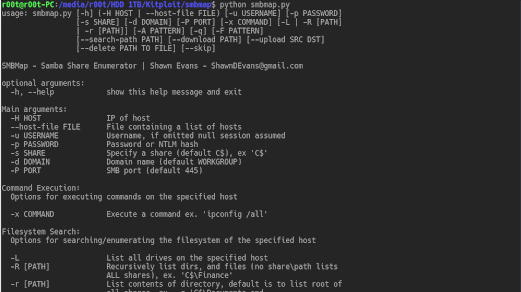
SMBMap allows users to enumerate samba share drives across an entire domain. List share drives, drive permissions, share contents, upload/download...
The objective of this program is to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines...
Windows’ BITS service is a middleman for your download jobs. You start a BITS job, and from that point on, BITS is responsible for the download. But what if we...
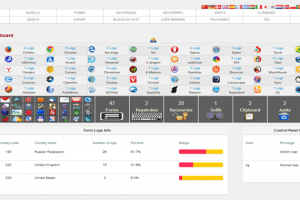
It seems sophisticated hackers have changed the way they conduct targeted cyber operations—instead of investing in zero-days and developing their malware; some...