Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
Search Results For - Malware
Cybercriminals are known to take advantage of everything that’s popular among people in order to spread malware, and Google’s official Play Store...
Cybercriminals decided to use the Search Engine Optimization (SEO) to make their malicious links more widespread in the search results, allowing them to gain...
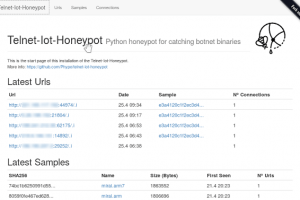
This project implements a python telnet server trying to act as a honeypot for IoT Malware which spreads over horribly insecure default passwords on telnet...
In 2013, Hackers apparently gained access to the Trump Organization’s domain booking account and created at least 250 website subdomains that cybersecurity...
Diamorphine is a LKM rootkit for Linux Kernels 2.6.x/3.x/4.x Features When loaded, the module starts invisible; Hide/unhide any process by sending a signal 31;...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
The flaw was discovered by researchers from Check Point in the user authentication method between the SmartThinQ portable app and LG’s back-end platform. This...
The British government has admitted publicly for the first time that it is all but certain North Korea carried out the “WannaCry” malware attack...
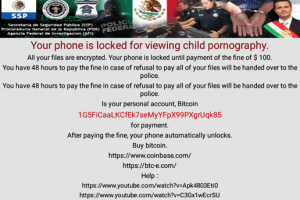
Security researchers from SfyLabs have detected an Android banking trojan dubbed LokiBot that transforms itself into a complete ransomware once the targeted...