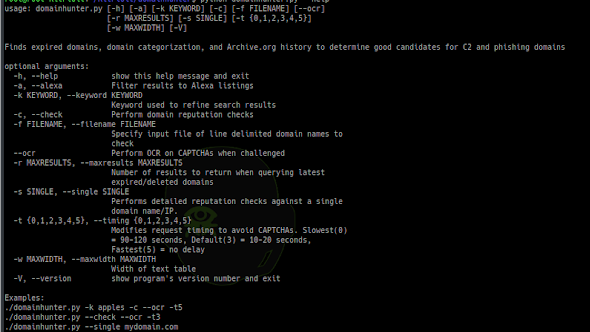
Domain name selection is an important aspect of preparation for penetration tests and especially Red Team engagements. Commonly, domains that were used...
Search Results For - Mac OS X
[sc name=”ad_1″] This may sound crazy, but it’s true! The war for “most-subscribed Youtube channel” crown between T-Series and...
[sc name=”ad_1″] Cybersecurity researchers have discovered a new zero-day vulnerability in Adobe Flash Player that hackers are actively exploiting...
Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...
ACHE is a focused web crawler. It collects web pages that satisfy some specific criteria, e.g., pages that belong to a given domain or that contain a user...
Here’s the main new features and improvements in Faraday v3.3: Workspace archive You are now able to make the whole workspace read only and archive it for...
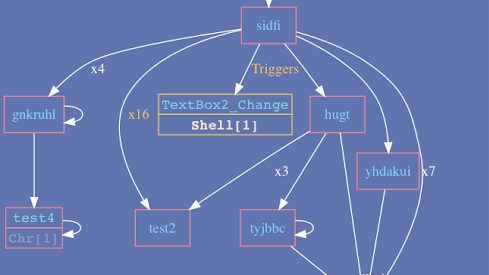
A tool for security researchers, who waste their time analyzing malicious Office macros. Generates a VBA call graph, with potential malicious keywords...
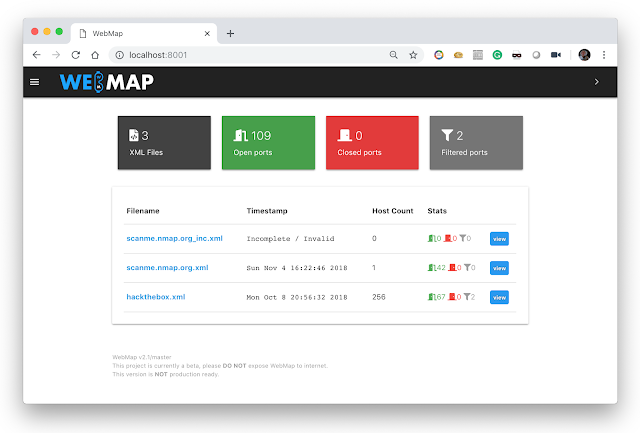
A Web Dashbord for Nmap XML Report Usage You should use this with docker, just by sending this command: $ mkdir /tmp/webmap $ docker run -d --name webmap -h...
novahot is a webshell framework for penetration testers. It implements a JSON-based API that can communicate with trojans written in any language. By default...
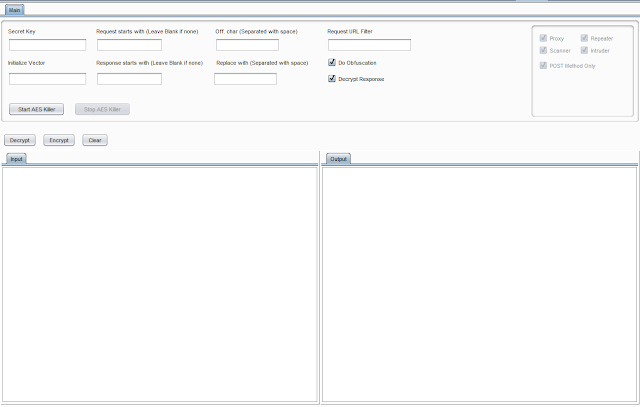
Burpsuite Plugin to decrypt AES Encrypted traffic on the fly. Requirements Burpsuite Java Tested on Burpsuite 1.7.36 Windows 10 xubuntu 18.04 Kali Linux 2018...