Belati is tool for Collecting Public Data & Public Document from Website and other service for OSINT purpose. This tools is inspired by Foca and Datasploit...
Search Results For - Mac OS X
Attack vectors There are 4 attack vectors available: beacon creds meterpreter meterpreter-grant For the ‘creds’ method, macphish can generate the Applescript...
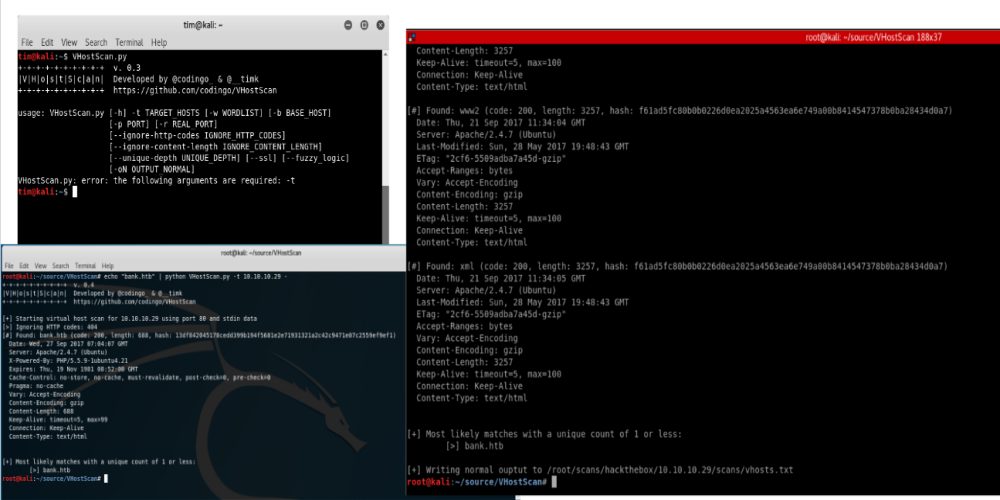
A virtual host scanner that can be used with pivot tools, detect catch-all scenarios, aliases and dynamic default pages. First presented at SecTalks BNE in...
[sc name=”ad_1″] Utility to find AES keys in running process memory. Works for 128, 192 and 256-bit keys. Usage Open aes-finder.sln solution in...
[sc name=”ad_1″] FATT is a script for extracting network metadata and fingerprints such as JA3 and HASSH from packet capture files (pcap) or live...
[sc name=”ad_1″] Great news. If you have already installed the latest update of Google Play Services released earlier today, and your Android...
[sc name=”ad_1″] For all of the undeniable conveniences the Internet has brought us, it’s becoming an increasingly dangerous place to be...
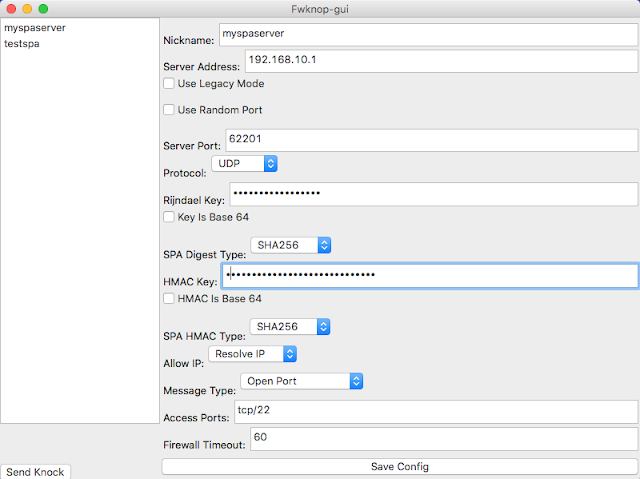
[sc name=”ad_1″] fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires...
[sc name=”ad_1″] Beware! If you have downloaded PHP PEAR package manager from its official website in past 6 months, we are sorry to say that your...
Nubia is a lightweight framework for building command-line applications with Python. It was originally designed for the “logdevice interactive shell (aka...