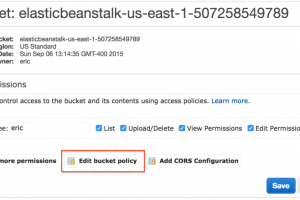
Discovered by UpGuard defense researcher Chris Vickery, the databases were entitled “CENTCOM-backup,” “CENTCOM-archive,” and “pacom-archive.” Based on their...
Search Results For - Logs
Prochunter aims to find hidden process with all userspace and most of the kernelspace rootkits. This tool is composed of a kernel module that prints out all...
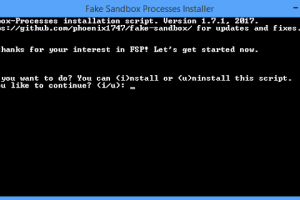
This small script will simulate fake processes of analysis, sandbox and/or VM software that some malware will try to avoid. You can download the original...
Adobe’s latest security update has swatted a total of 67 bugs, some of them critical, in Adobe Flash, Acrobat, and Reader. On Tuesday, the software...
Nishang is an open source framework and collection of powerful PowerShell scripts and payloads that you can use during penetration testing audit, post...
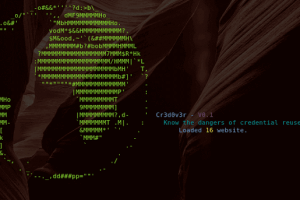
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...
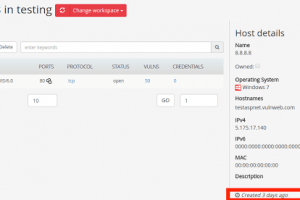
Just over a month after OnePlus was caught collecting personally identifiable information on its users, the Chinese smartphone company has been found leaving a...
Faraday is the Integrated Multiuser Risk Environment you have always been looking for! It maps and leverages all the data you generate in real time, letting...
A pattern based Dalvik deobfuscator which uses limited execution to improve semantic analysis. Also, the inspiration for another Android deobfuscator: Simplify...
Evil-Droid is a framework that create & generate & embed apk payload to penetrate android platforms. Screenshot: Dependencies : 1 - metasploit...