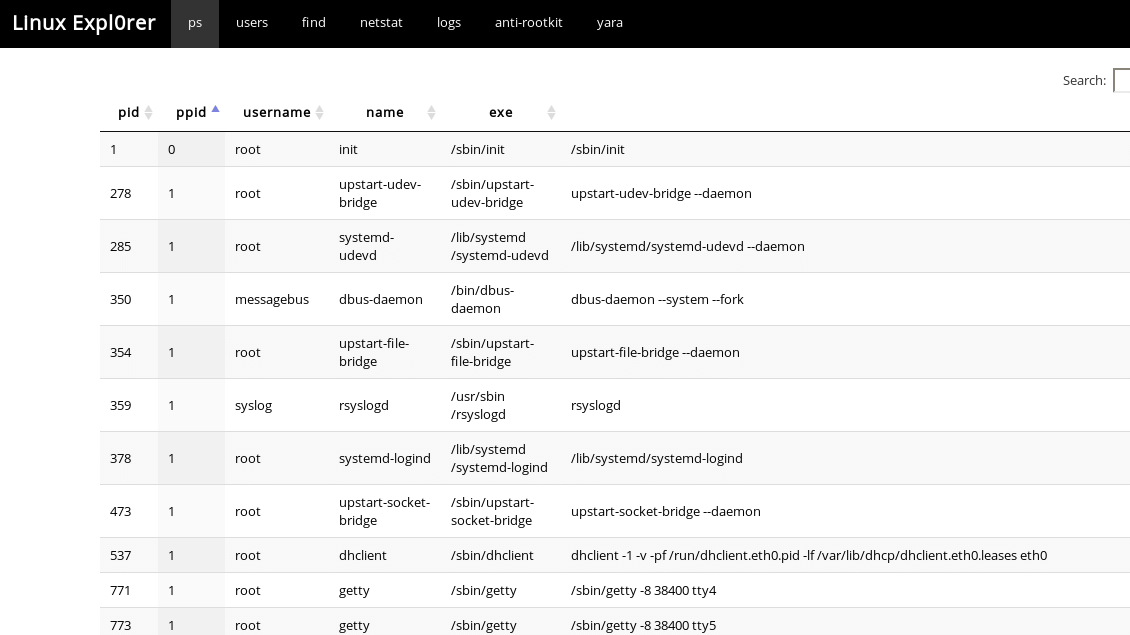
Easy-to-use live forensics toolbox for Linux endpoints written in Python & Flask. Capabilities ps View full process list Inspect process memory map &...
Search Results For - Logs
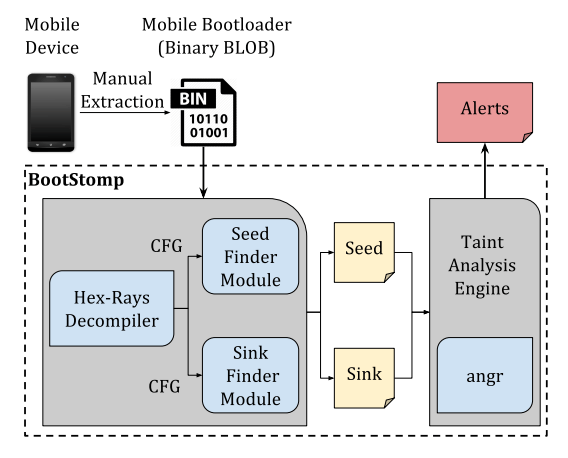
BootStomp is a boot-loader bug finder. It looks for two different class of bugs: memory corruption and state storage vulnerabilities. For more info please...
Bitcoin is breaking every record—after gaining 20% jump last week, Bitcoin price just crossed the $14,800 mark in less than 24 hours—and there can be no better...
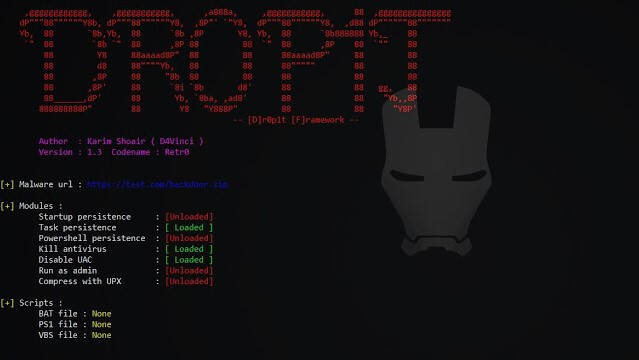
Have you ever heard about trojan droppers ? In short dropper is type of malware that downloads other malwares and Dr0p1t gives you the chance to create a...
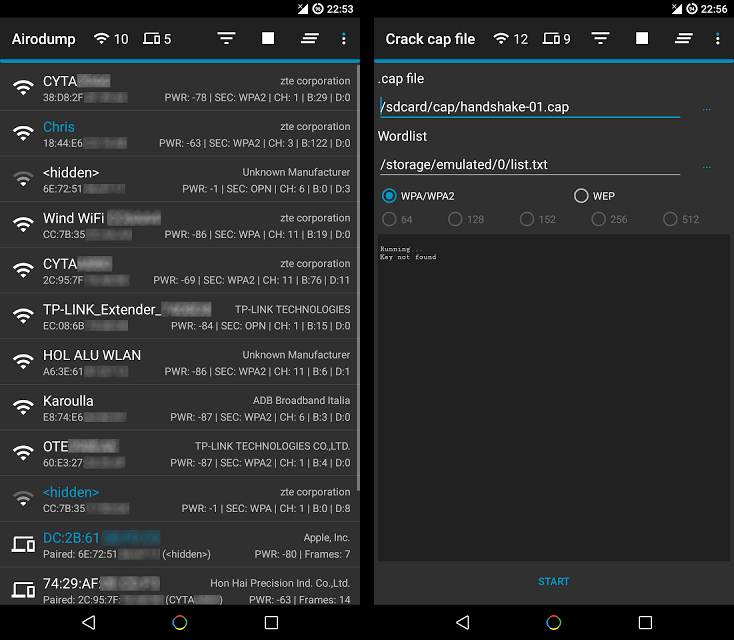
Hijacker is a Graphical User Interface for the penetration testing tools Aircrack-ng, Airodump-ng, MDK3 and Reaver. It offers a simple and easy UI to use these...
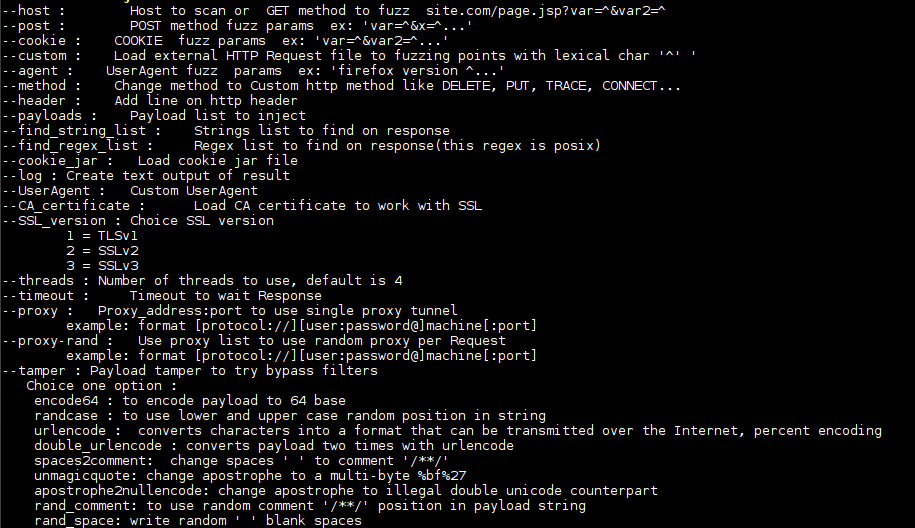
Web security tool to make fuzzing at HTTP inputs, made in C with libCurl. 0d1n is a tool for automating customized attacks against web applications. You can...
ratched is a Man-in-the-Middle (MitM) proxy that specifically intercepts TLS connections. It is intended to be used in conjunction with the Linux iptables...
Security Tool to detect arp poisoning attacks. Features Uses a faster approach in detection of arp poisoning attacks compared to passive approaches Detects not...
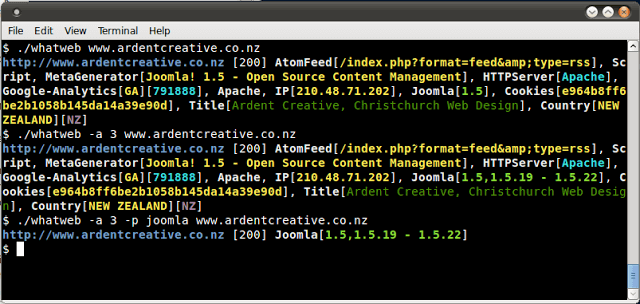
WhatWeb identifies websites. Its goal is to answer the question, “What is that Website?”. WhatWeb recognises web technologies including content management...
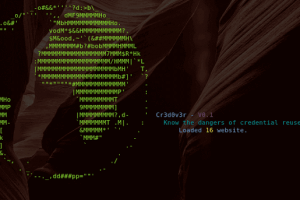
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...