[sc name=”ad_1″] Hold tight, this may blow your mind… A low-privileged user account on most Linux operating systems with UID value anything greater...
Search Results For - Logs
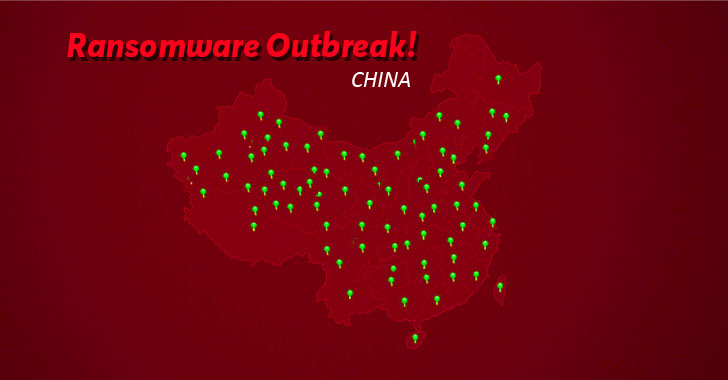
A new piece of ransomware is spreading rapidly across China that has already infected more than 100,000 computers in the last four days as a result of a supply...
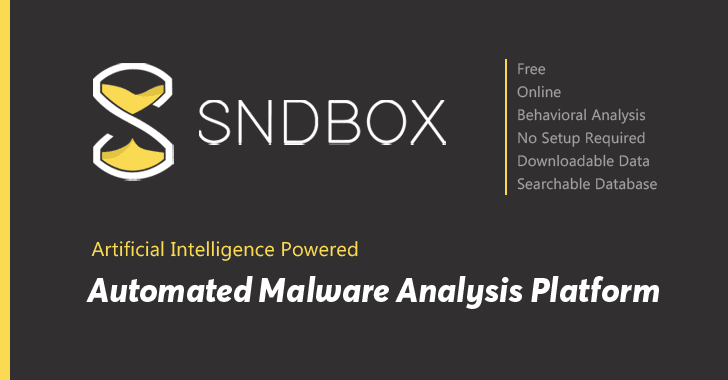
Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...
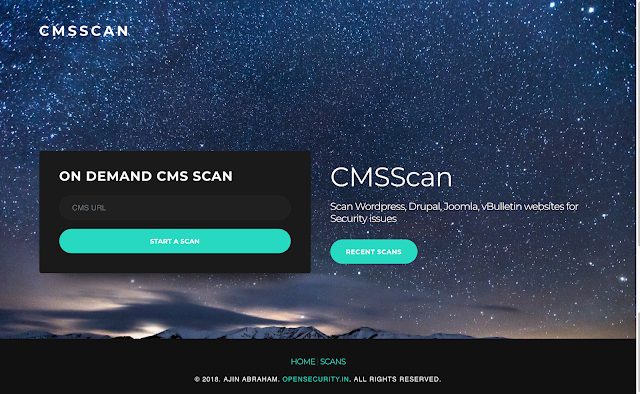
Scan WordPress, Drupal, Joomla, vBulletin websites for Security issues. CMSScan provides a centralized Security Dashboard for CMS Security scans. It is powered...
ACHE is a focused web crawler. It collects web pages that satisfy some specific criteria, e.g., pages that belong to a given domain or that contain a user...
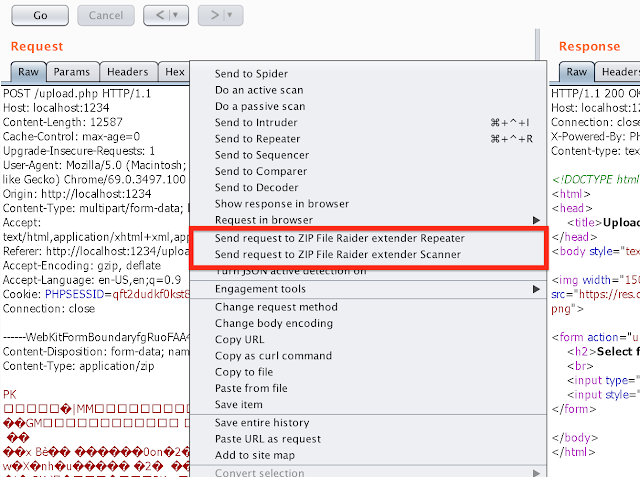
ZIP File Raider is a Burp Suite extension for attacking web application with ZIP file upload functionality. You can easily inject Burp Scanner/Repeater...
Here’s the main new features and improvements in Faraday v3.3: Workspace archive You are now able to make the whole workspace read only and archive it for...
CAINE (Computer Aided INvestigative Environment) is an Italian GNU/Linux live distribution created as a Digital Forensics project. Currently, the project...
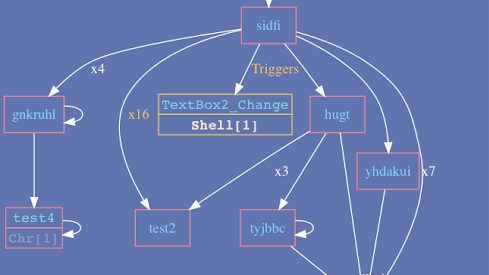
A tool for security researchers, who waste their time analyzing malicious Office macros. Generates a VBA call graph, with potential malicious keywords...
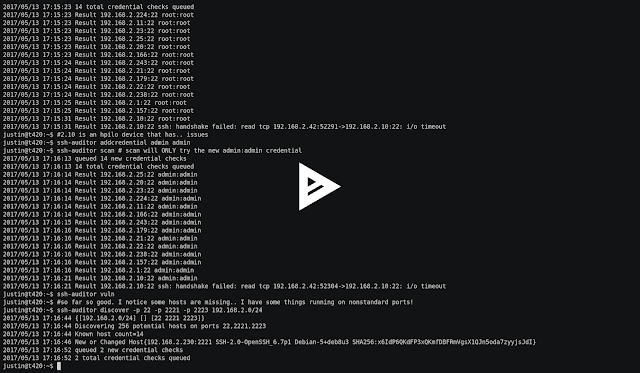
The Best Way To Scan For Weak Ssh Passwords On Your Network Features ssh-auditor will automatically: Re-check all known hosts as new credentials are added. It...