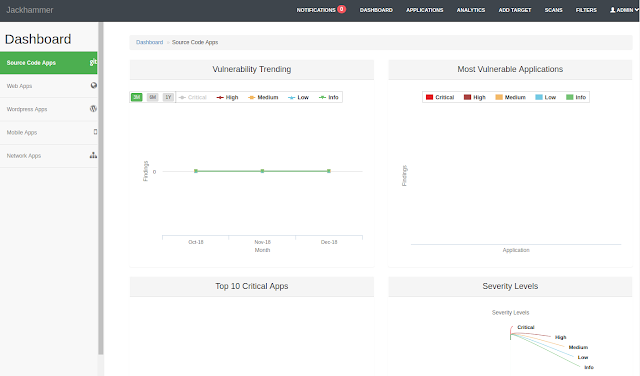
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...
Search Results For - Logs
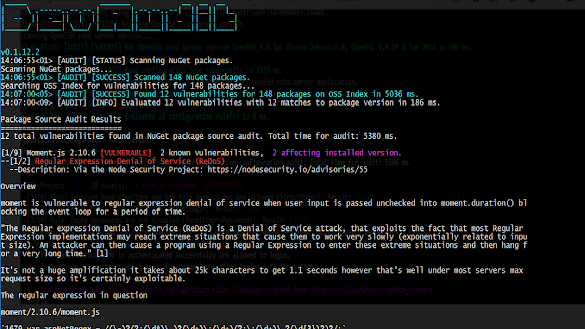
[sc name=”ad_1″] DevAudit is an open-source, cross-platform, multi-purpose security auditing tool targeted at developers and teams adopting DevOps...
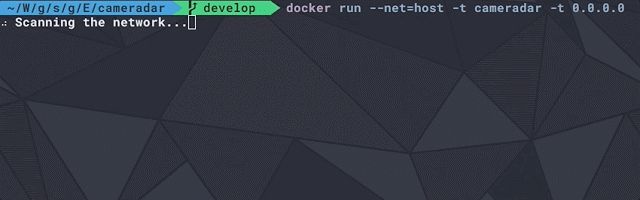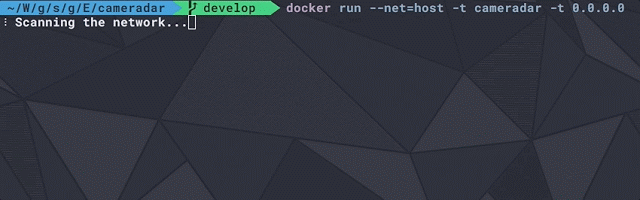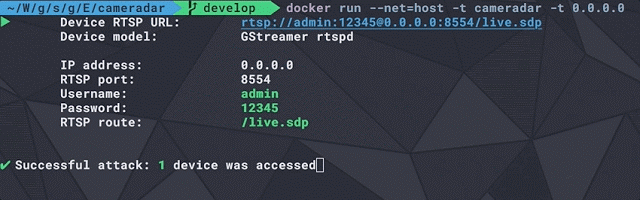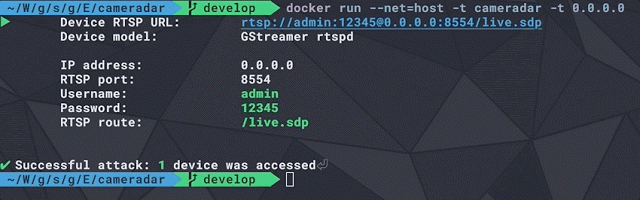
[sc name=”ad_1″] An RTSP stream access tool that comes with its library Cameradar allows you to Detect open RTSP hosts on any accessible target...
[sc name=”ad_1″] Two hackers have been sent to prison for their roles in hacking TalkTalk, one of the biggest UK-based telecommunications company...
[sc name=”ad_1″] It seems as though not a day goes by without a new story breaking about a high-level cyber attack on a major corporation or...
[sc name=”ad_1″] The real identity of Tessa88—the notorious hacker tied to several high-profile cyber attacks including the LinkedIn, DropBox and...
[sc name=”ad_1″] Cheetah Mobile—a prominent Chinese app company, known for its popular utility apps like Clean Master and Battery Doctor—and one of...
[sc name=”ad_1″] Google, the FBI, ad-fraud fighting company WhiteOps and a collection of cyber security companies worked together to shut down one...
[sc name=”ad_1″] The Department of Justice announced Wednesday charges against two Iranian nationals for their involvement in creating and...
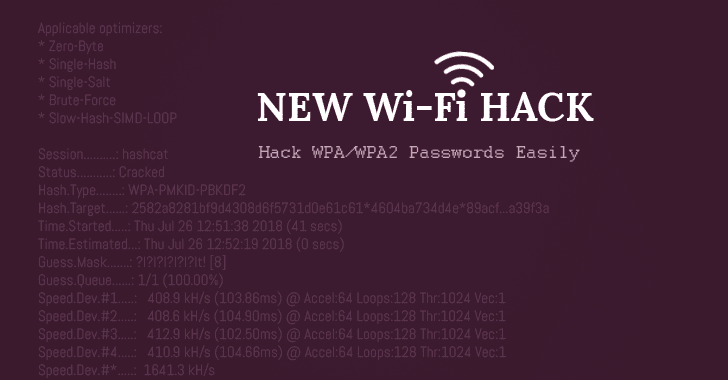
[sc name=”ad_1″] Looking for how to hack WiFi password OR WiFi hacking software? Well, a security researcher has revealed a new WiFi hacking...