[sc name=”ad_1″] Google has finally patched a privacy vulnerability in its Chrome web browser for Android that exposes users’ device model...
Search Results For - Logs
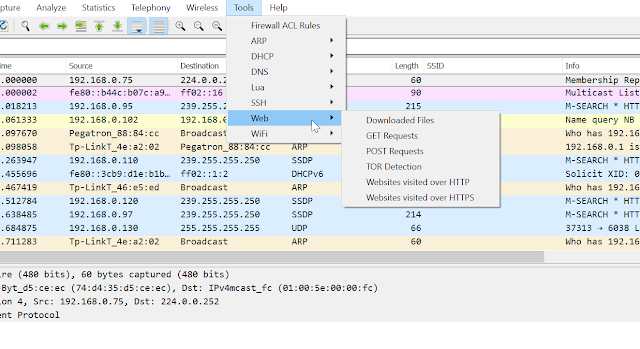
[sc name=”ad_1″] PA Toolkit is a collection of traffic analysis plugins to extend the functionality of Wireshark from a micro-analysis tool and...
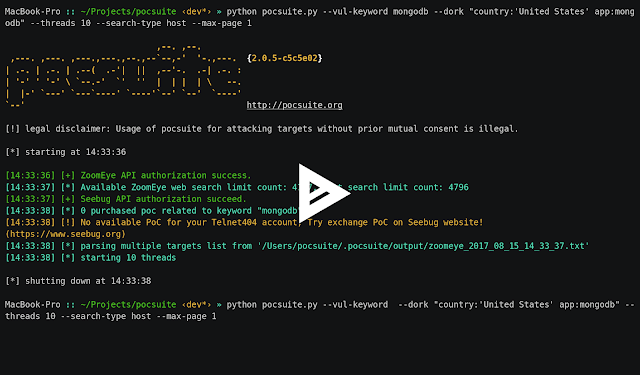
[sc name=”ad_1″] Pocsuite is an open-sourced remote vulnerability testing and proof-of-concept development framework developed by the Knownsec...
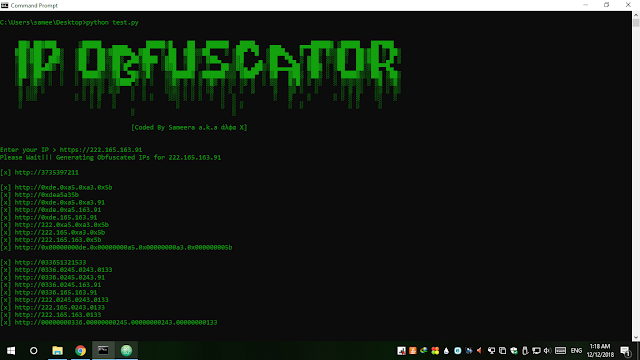
[sc name=”ad_1″] IP Obfuscator is a simple tool written in python to convert an IP into different obfuscated forms. This tool will help you to...
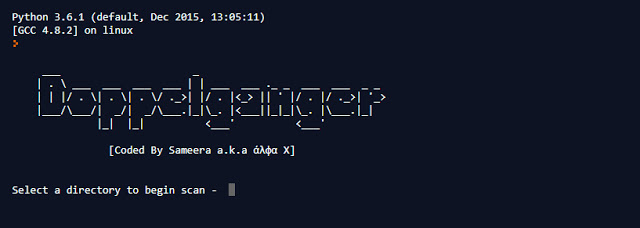
[sc name=”ad_1″] Doppelganger is a python script to scan duplicate copies in a given directory. This tool compare not only file names, but also...
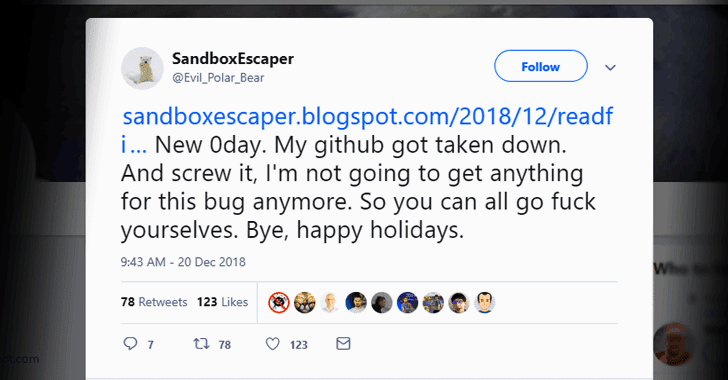
[sc name=”ad_1″] A security researcher with Twitter alias SandboxEscaper today released proof-of-concept (PoC) exploit for a new zero-day...
[sc name=”ad_1″] Another day, another data breach. This time it’s the United States National Aeronautics and Space Administration (NASA) NASA...
[sc name=”ad_1″] Security researchers have discovered yet another example of how cybercriminals disguise their malware activities as regular...
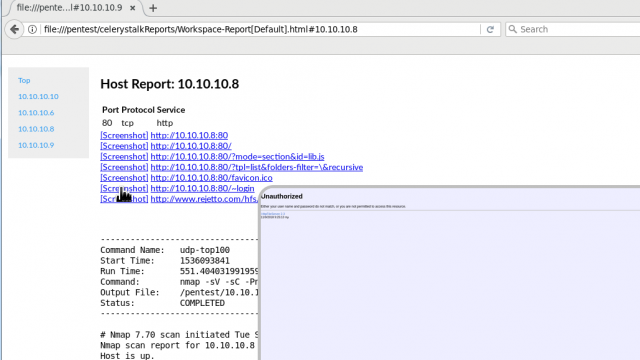
[sc name=”ad_1″] celerystalk helps you automate your network scanning/enumeration process with asynchronous jobs (aka tasks) while retaining full...
[sc name=”ad_1″] Facebook’s latest screw-up — a programming bug in Facebook website accidentally gave 1,500 third-party apps access to the...