[sc name=”ad_1″] An open-source binary debugger for Windows, aimed at malware analysis and reverse engineering of executables you do not have the...
Search Results For - Logs
[sc name=”ad_1″] This CLI framework is based on sploitkit and is an attempt to gather hacking techniques and exploits especially focused on drone...
[sc name=”ad_1″] ParamSpider : Parameter miner for humans. Key Features : Finds parameters from web archives of the entered domain. Finds...
[sc name=”ad_1″] The beginnings of a C2 framework. Currently without all the C2 stuff so far. Generates a dual stage VBS infection vector, and a...
[sc name=”ad_1″] Mail transfer is a common search query. Most commonly, users may migrate due to personal preferences, corporate policies, or...
[sc name=”ad_1″] Threat Dragon is a free, open-source, cross-platform threat modeling application including system diagramming and a rule engine to...
[sc name=”ad_1″] A typical search engine dork scanner that scrapes search engines with queries that you provide in order to find vulnerable URLs...
[sc name=”ad_1″] Shhgit finds secrets and sensitive files across GitHub code and Gists committed in near real time by listening to the GitHub...
[sc name=”ad_1″] Hardened Debian GNU/Linux and CentOS 8 distro auditing. The main test environment is in debian GNU/Linux 9/10 and CentOS 8, and...
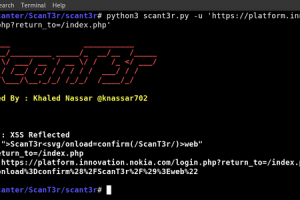
[sc name=”ad_1″] ScanT3r – Web Security Scanner _____ ___________ / ___/_________ _____/_ __/__ /_____ __ / ___/ __ `/ __ / / /_ </ ___/...